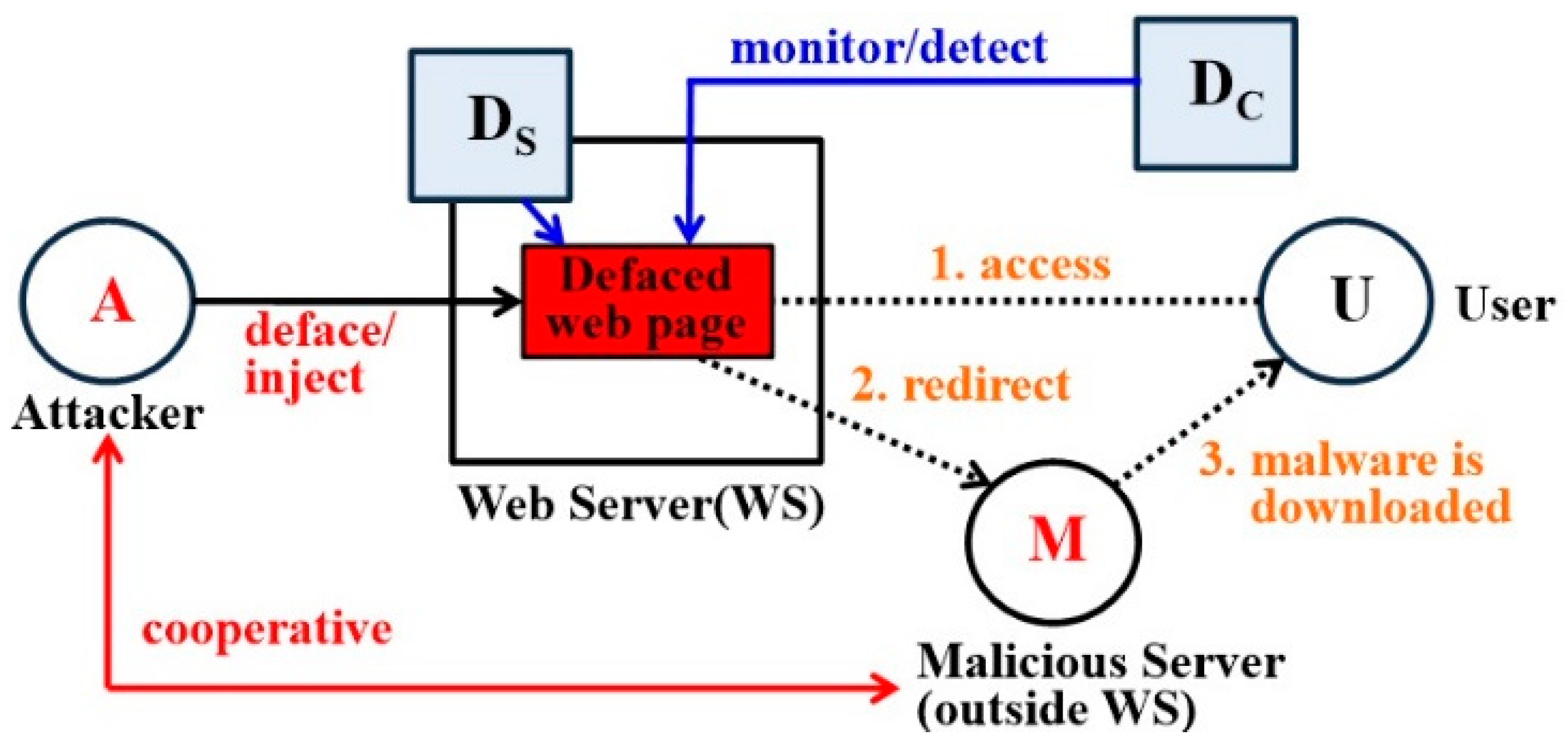
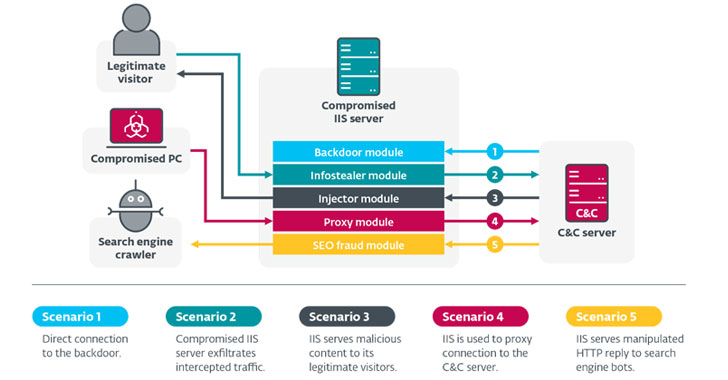
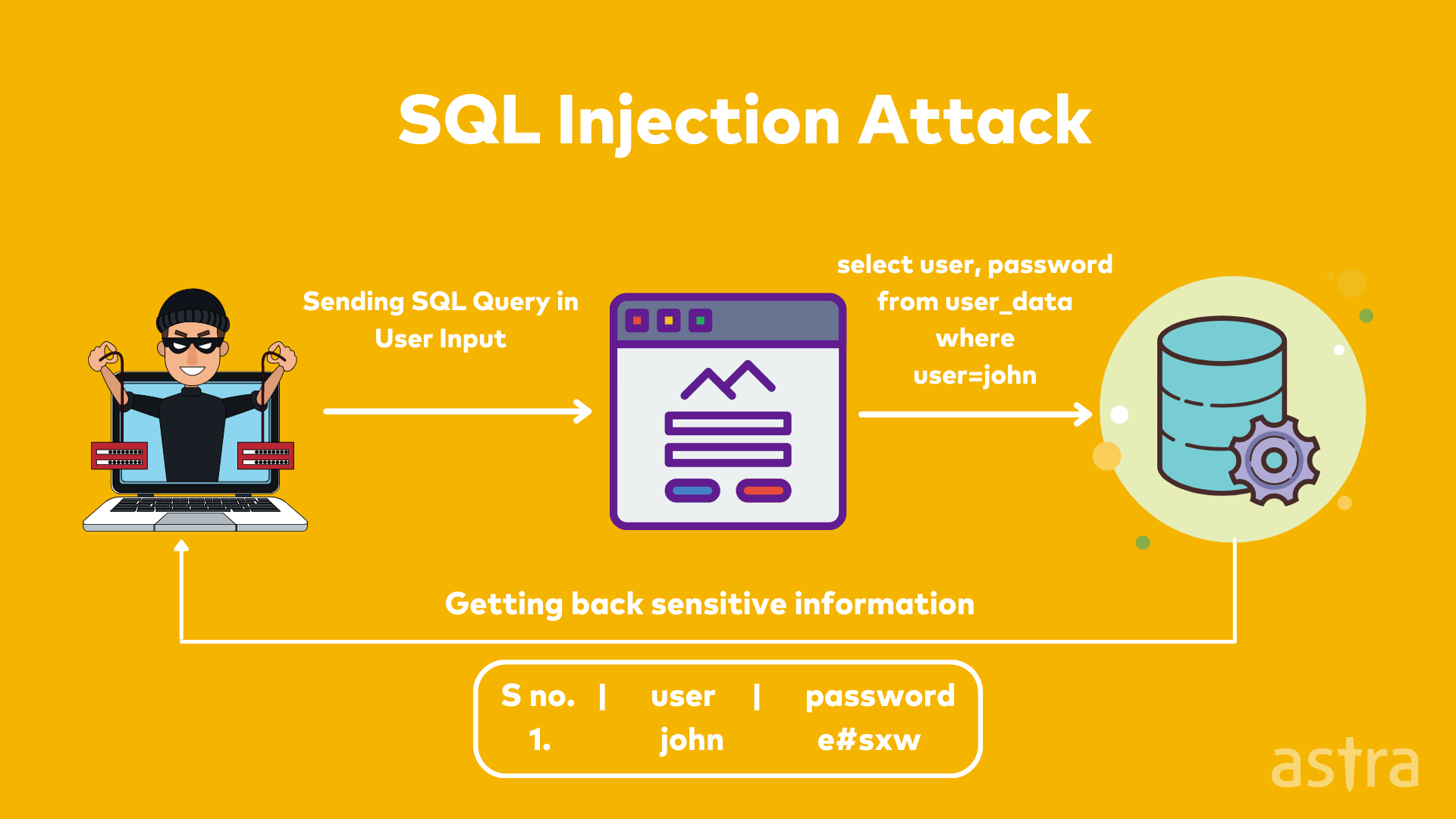
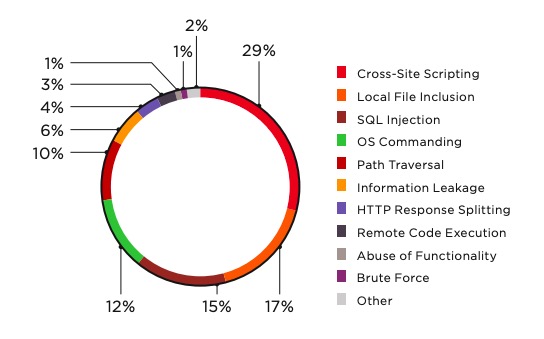
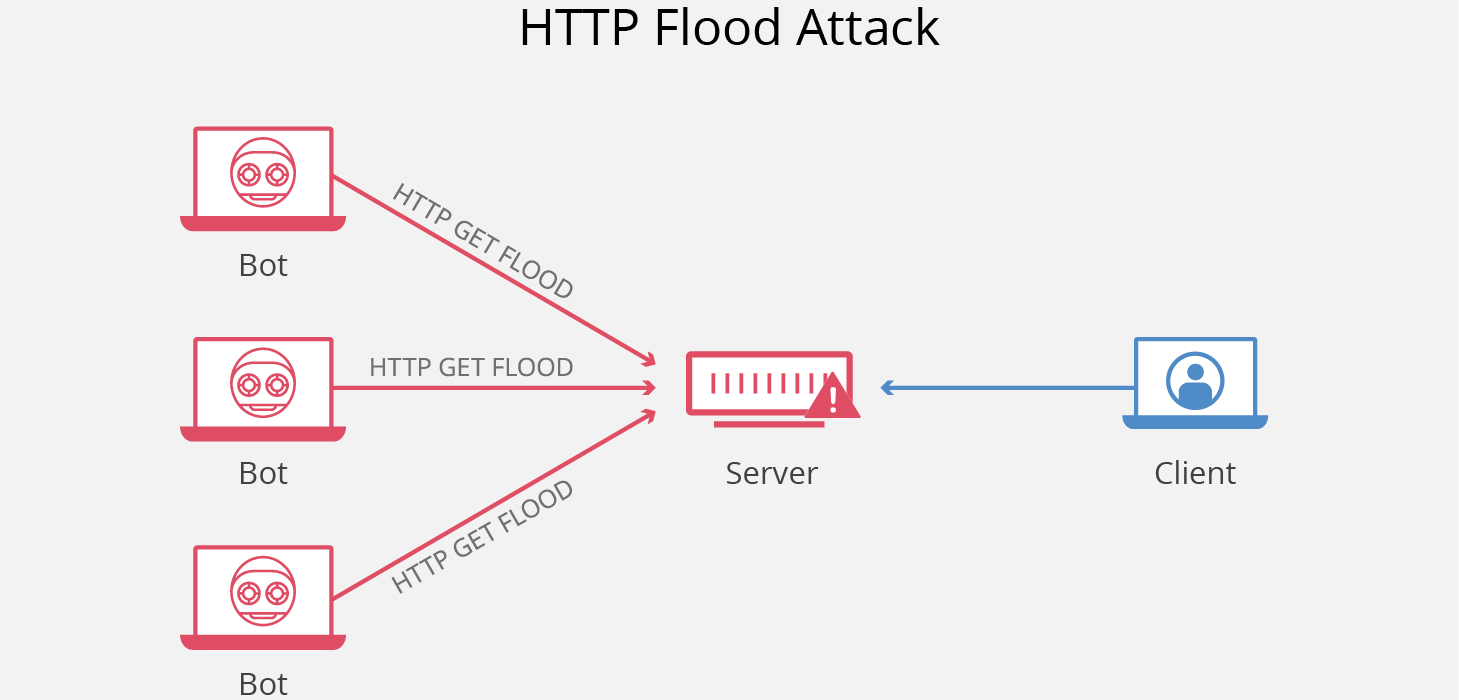
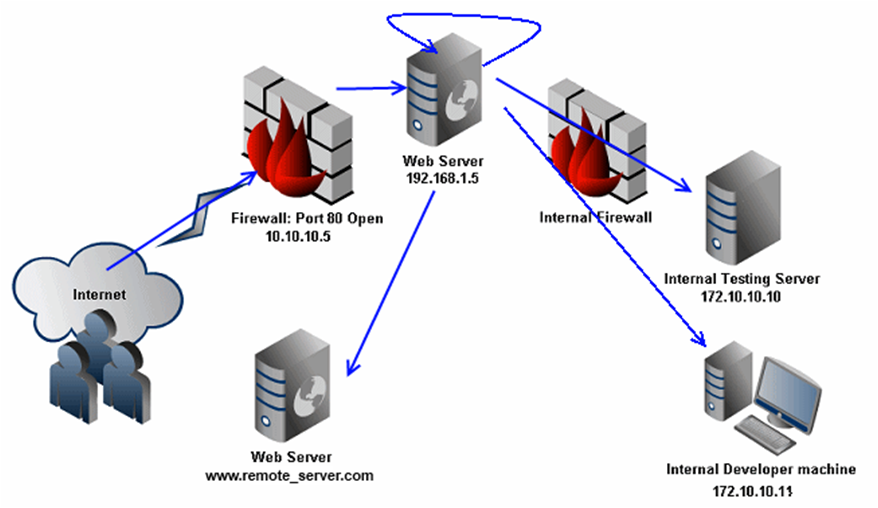
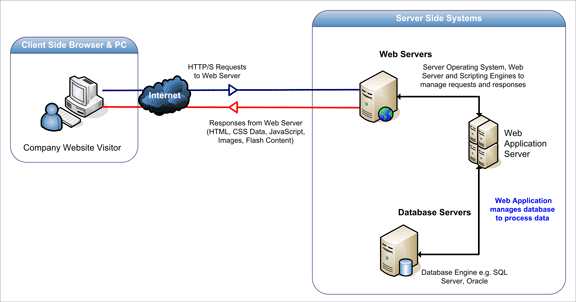
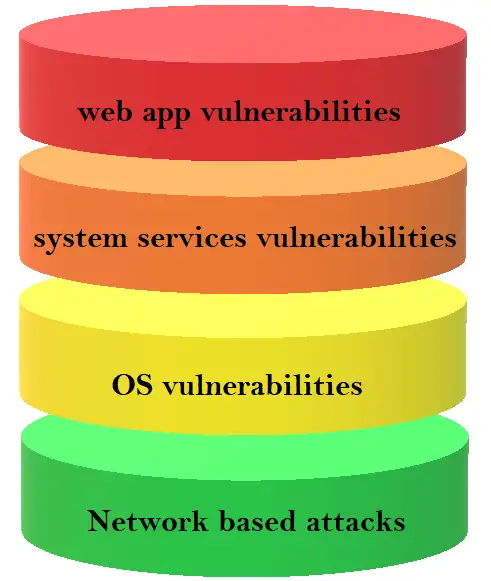
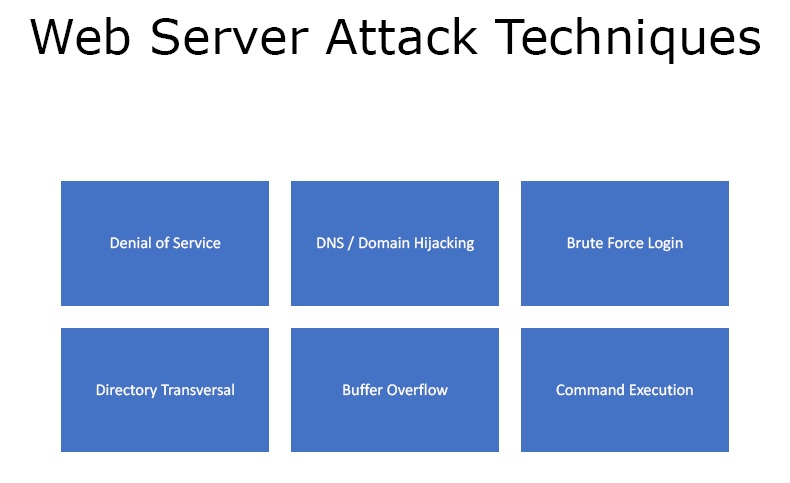
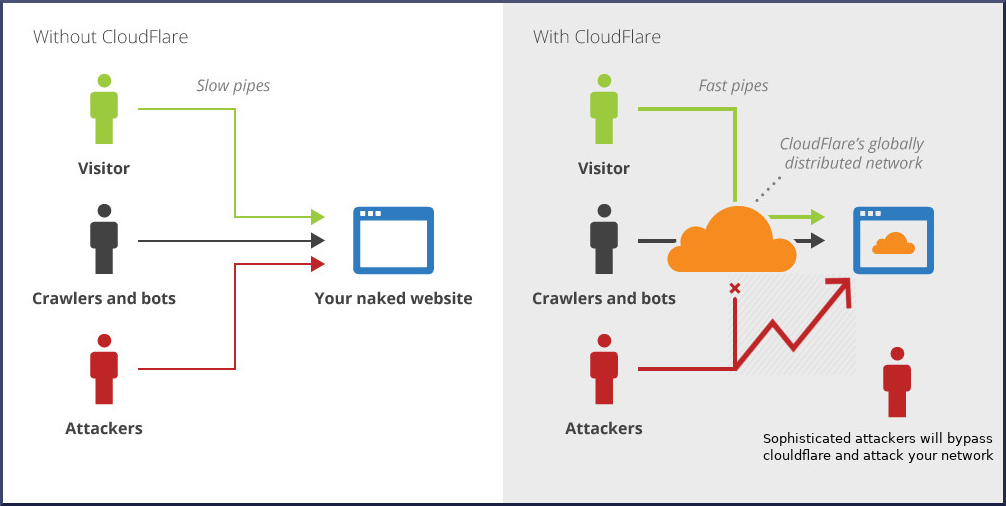
Experimental setup for DoS attacks on web server with Cisco ASA 5510... | Download Scientific Diagram
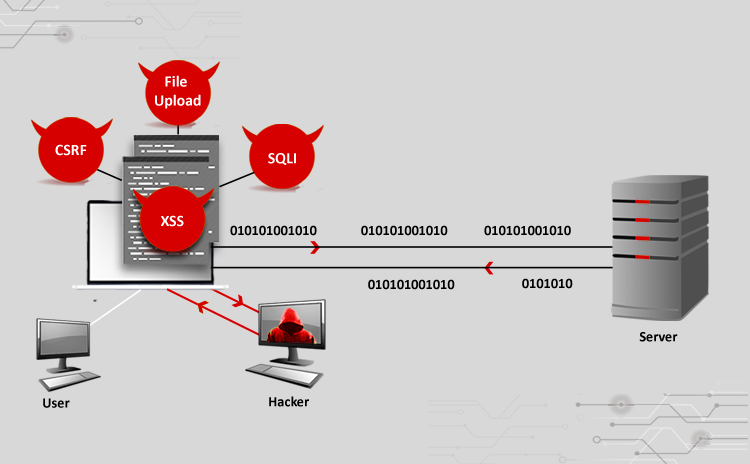
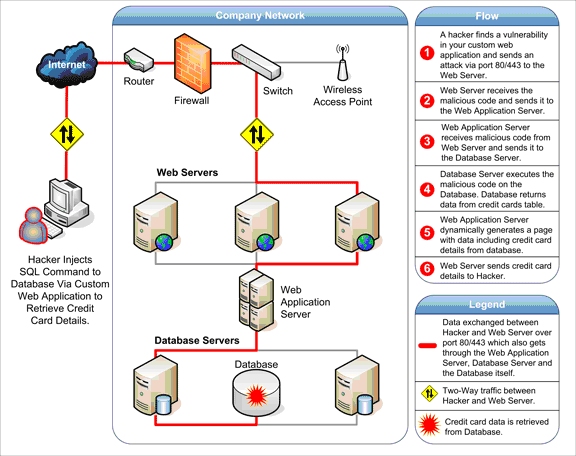
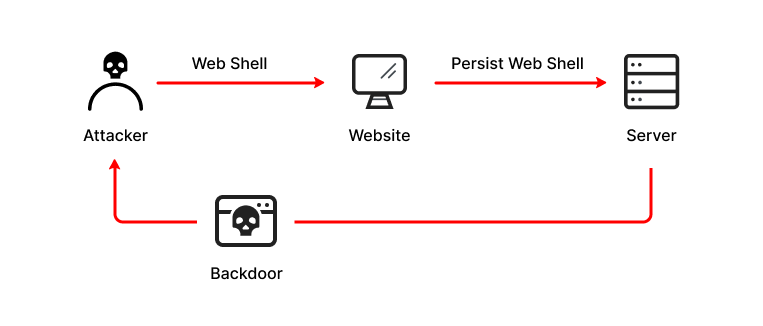
Cyber Attacks Explained - Web Exploitation - Cyber Security Blogs - Valency Networks - Best VAPT Penetration Testing Cyber Security Company - Pune Mumbai Hyderabad Delhi Bangalore Ahmedabad Kolkata India Dubai Bahrain

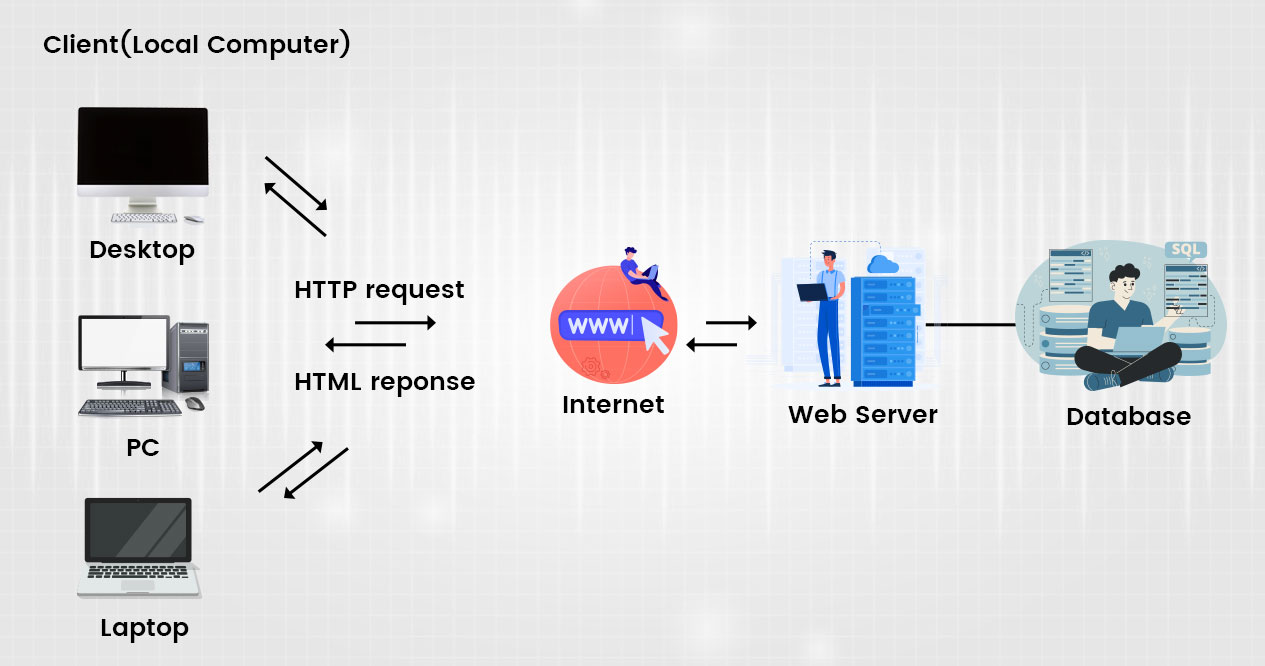
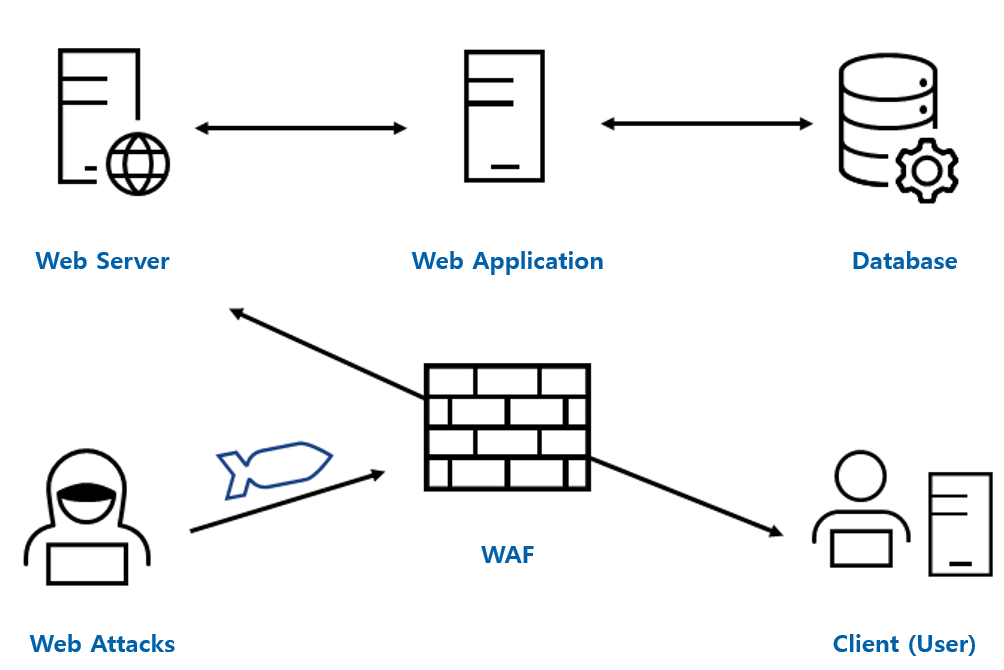
Sensors | Free Full-Text | Deep Learning Technique-Enabled Web Application Firewall for the Detection of Web Attacks