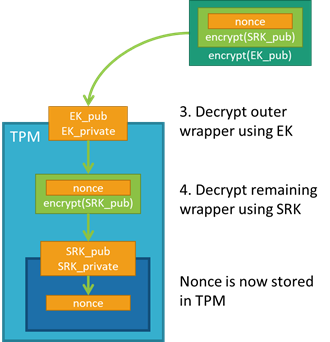
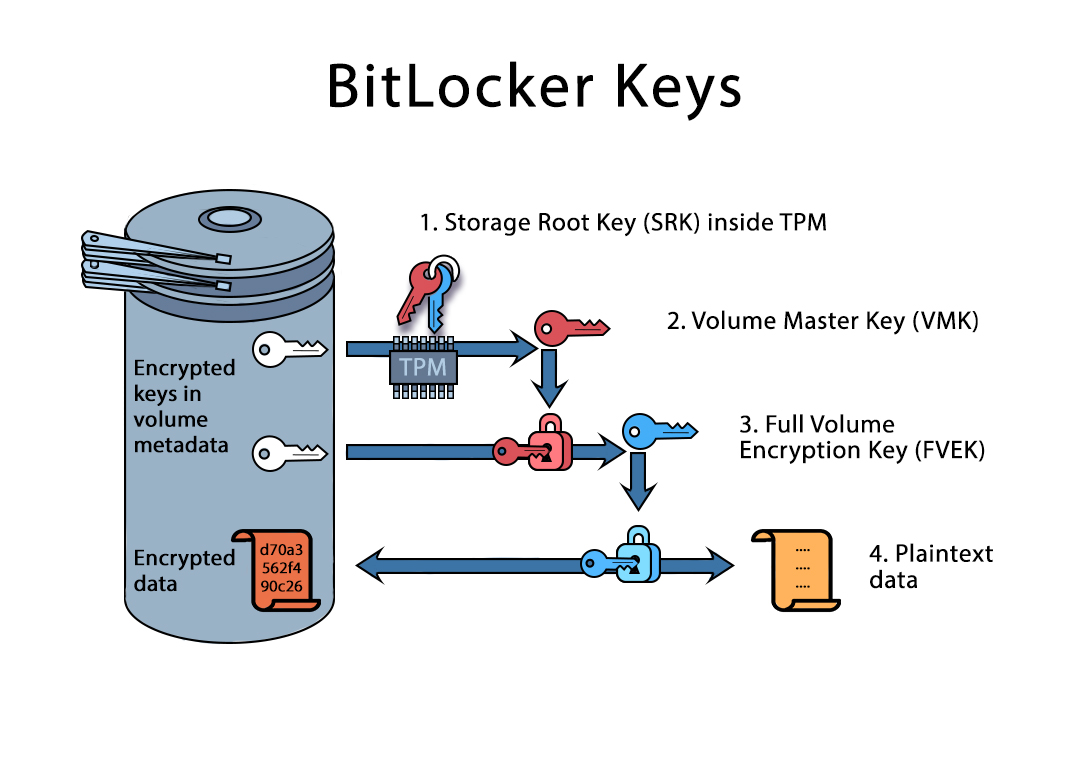
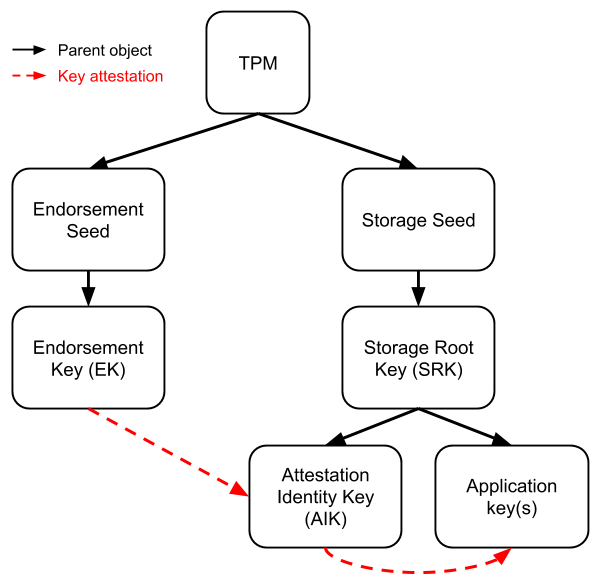
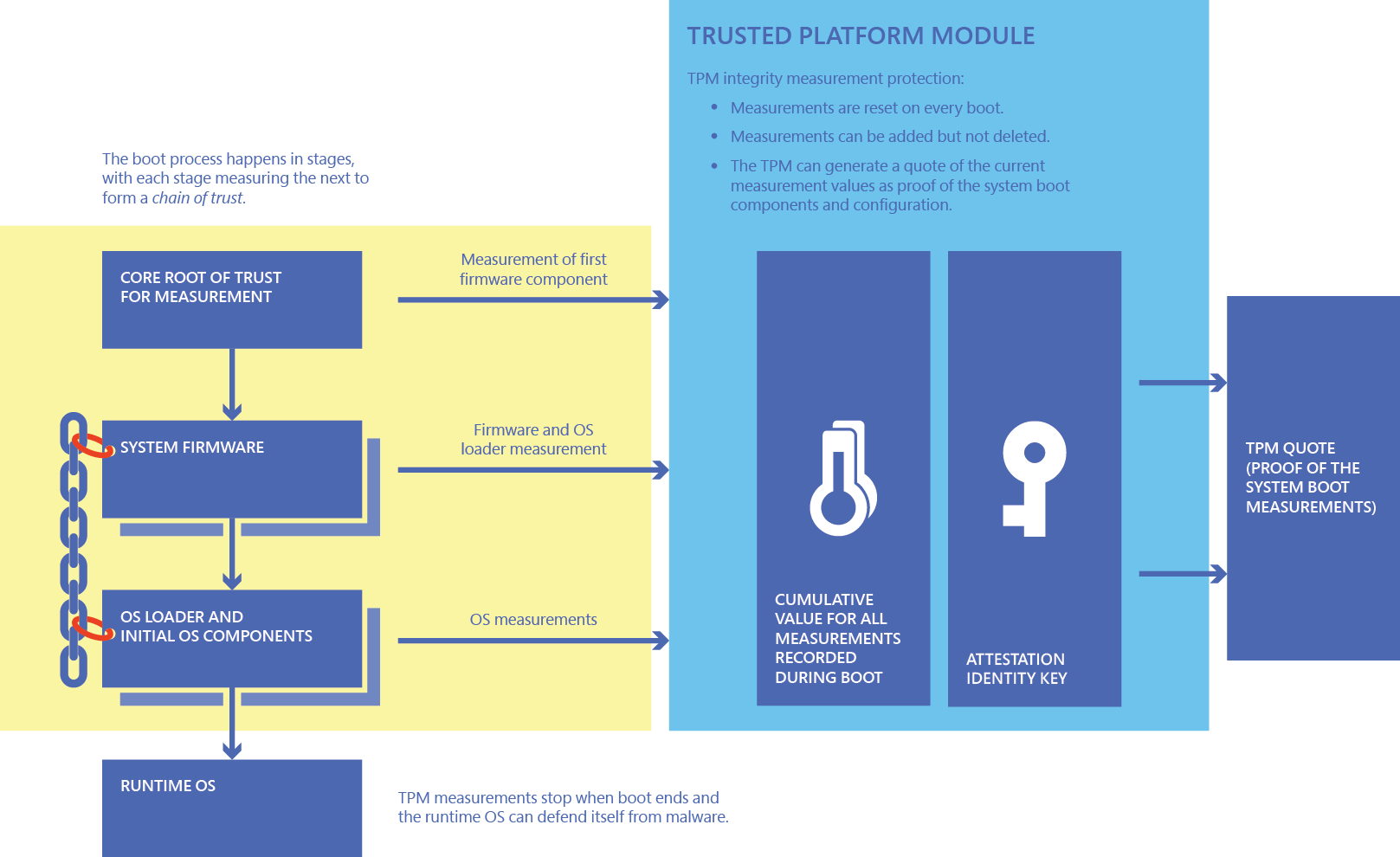
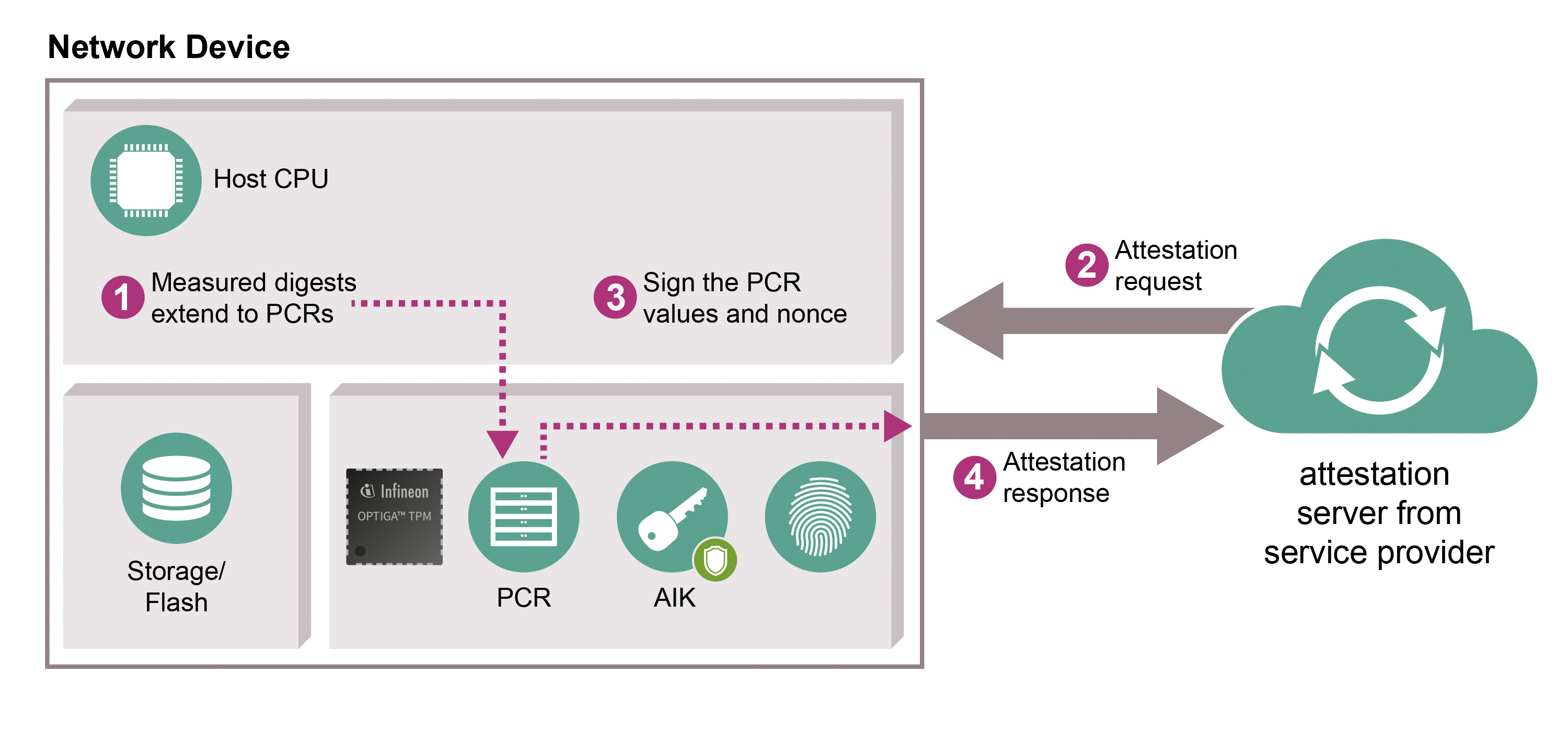
TKM Key Hierarchy Having in mind that TPM protected keys are bound to a... | Download Scientific Diagram
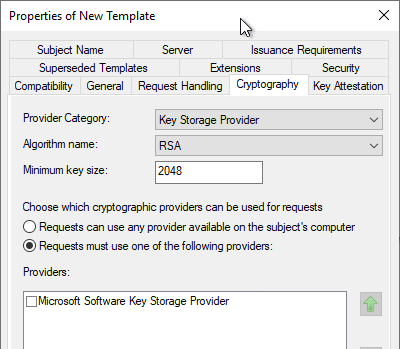
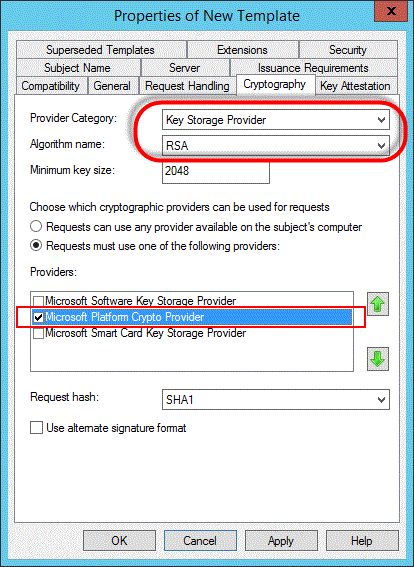
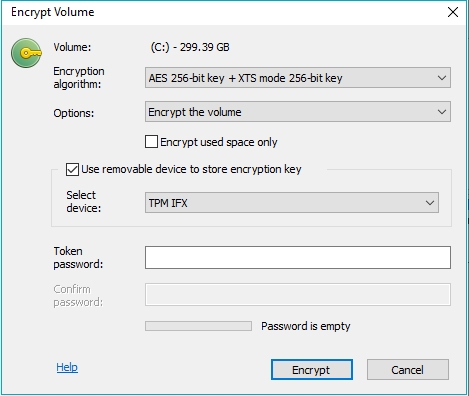
Konfigurieren einer Zertifikatvorlage für die Verwendung des Microsoft Platform Crypto Provider, um Schutz des privaten Schlüssels durch ein Trusted Platform Module (TPM) zu ermöglichen – Uwe Gradenegger

DirectAccess and Always On VPN with Trusted Platform Module (TPM) Certificates | Richard M. Hicks Consulting, Inc.

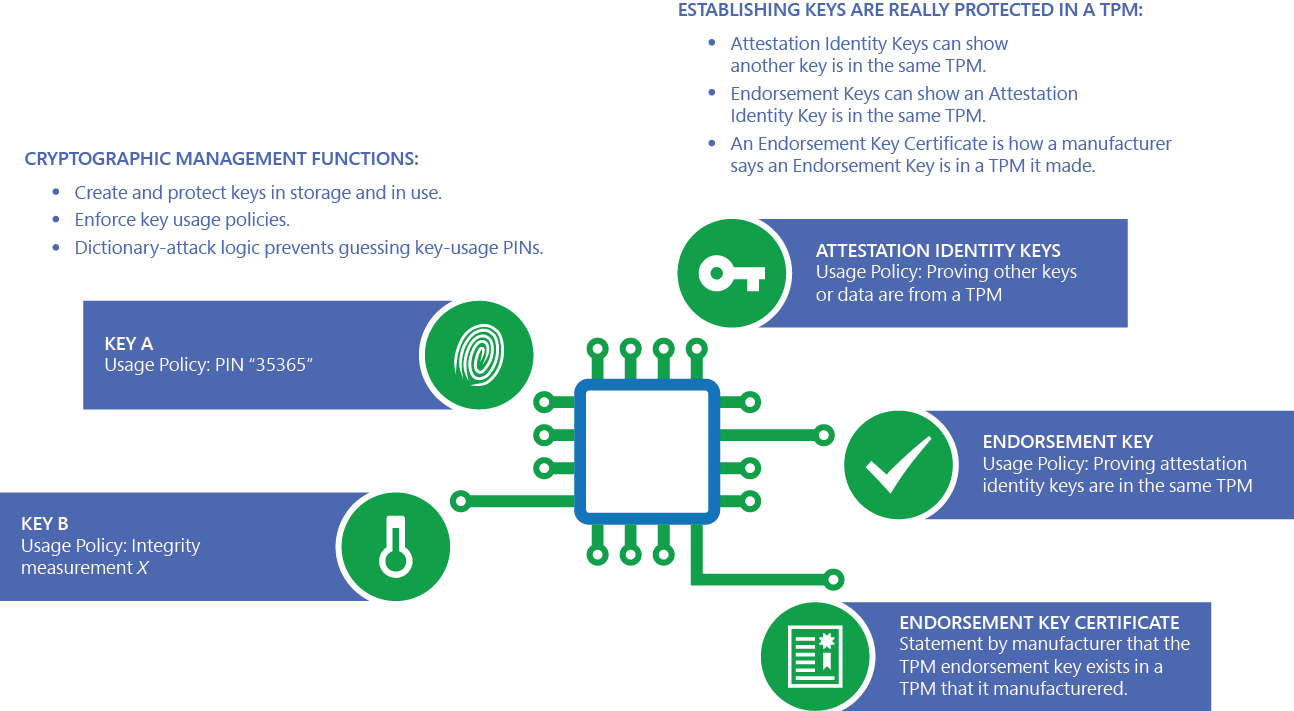
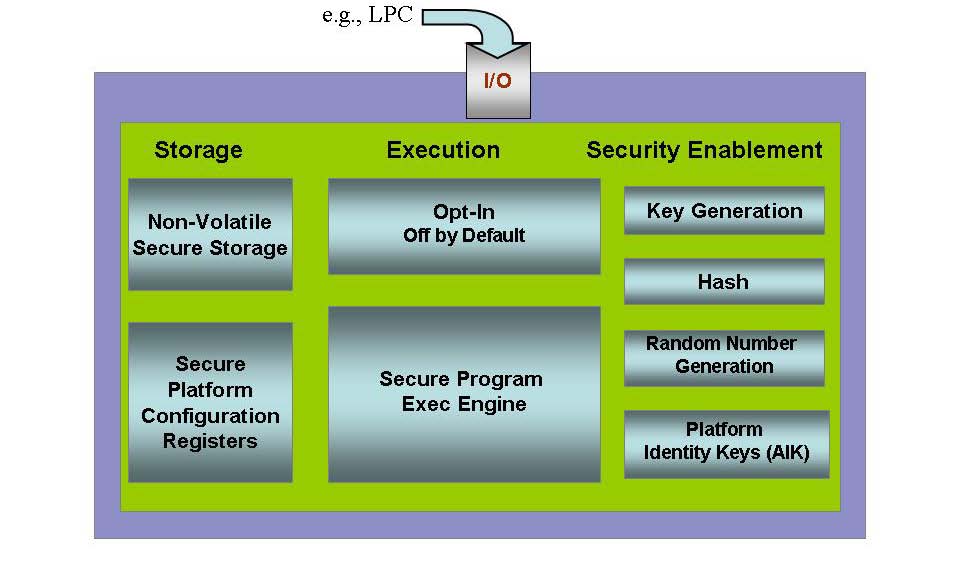
Basic Functionalities of a Trusted Platform | Trusted Computing Platforms, the Next Security Solution | InformIT

Using a Trusted Platform Module for endpoint device security in AWS IoT Greengrass | The Internet of Things on AWS – Official Blog