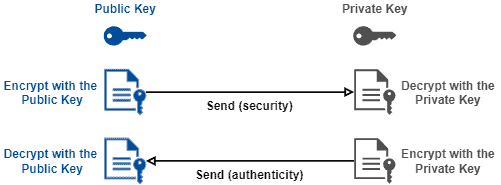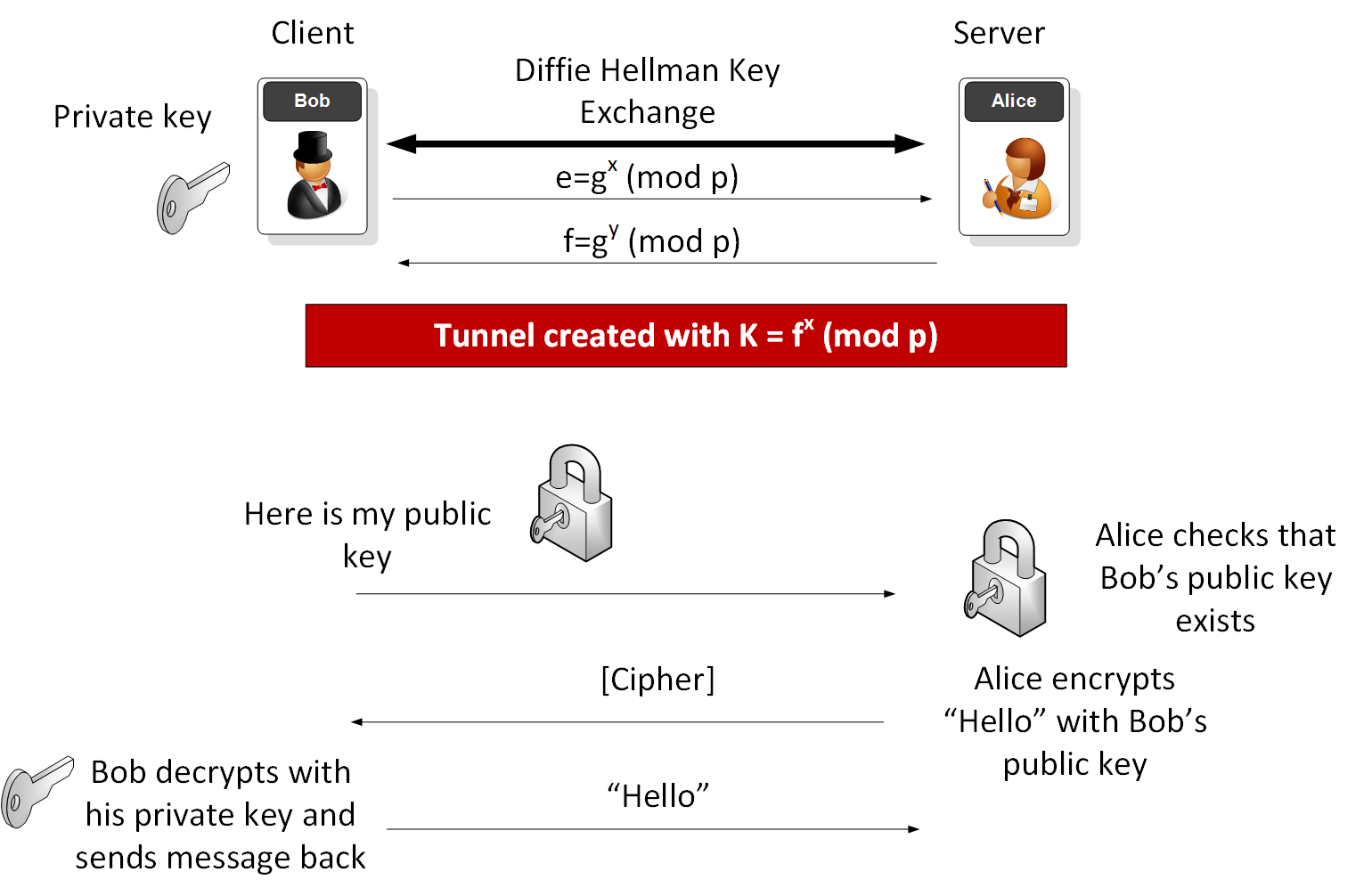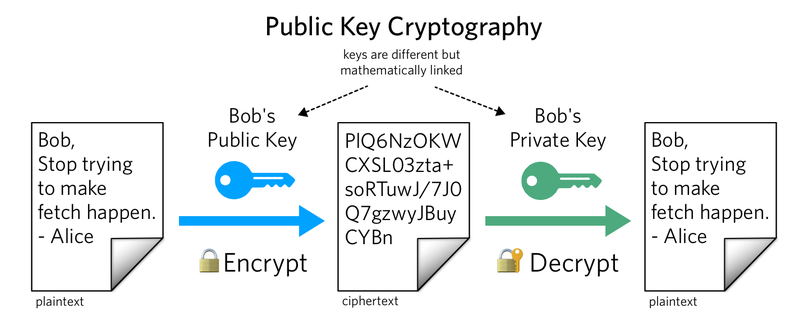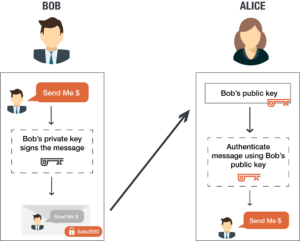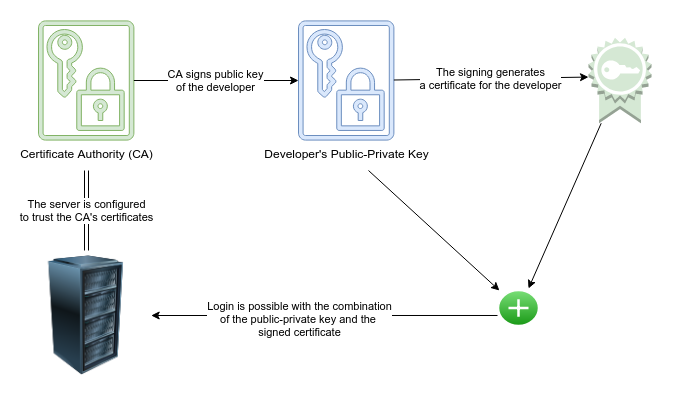
How to properly manage ssh keys for server access :: Päpper's Machine Learning Blog — This blog features state of the art applications in machine learning with a lot of PyTorch samples
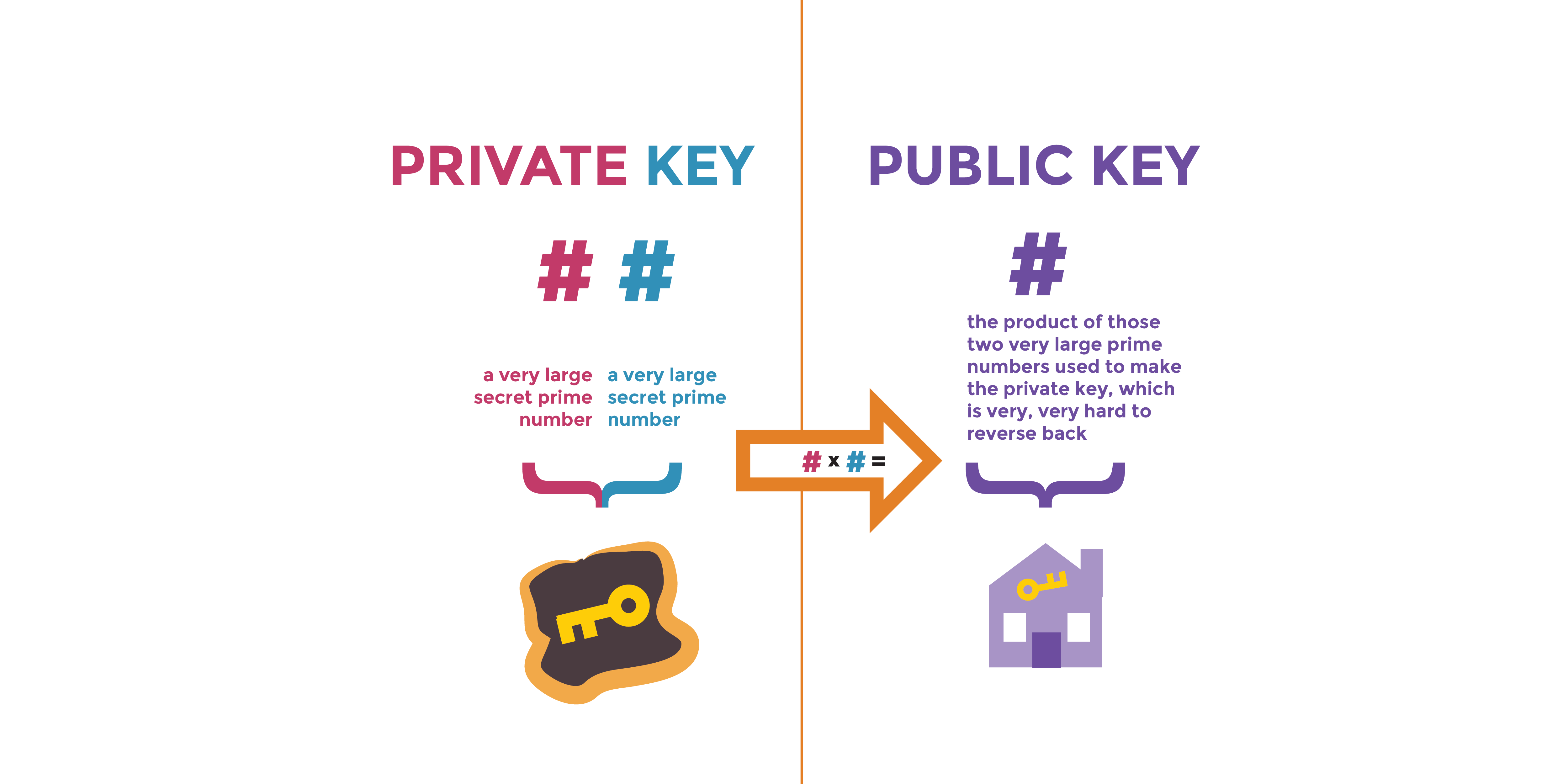
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense




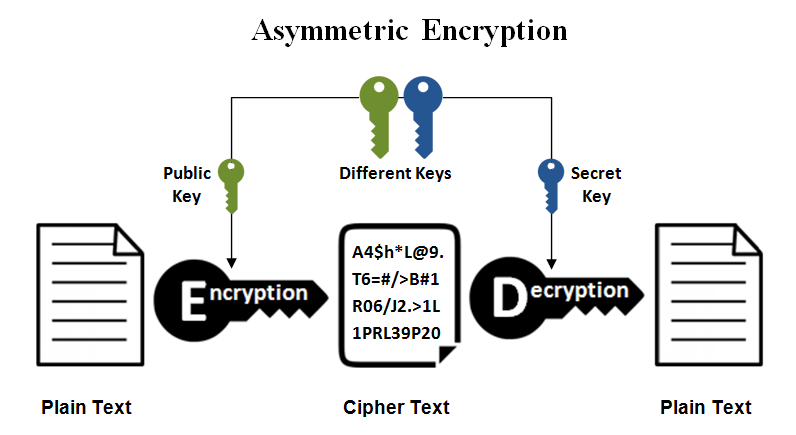



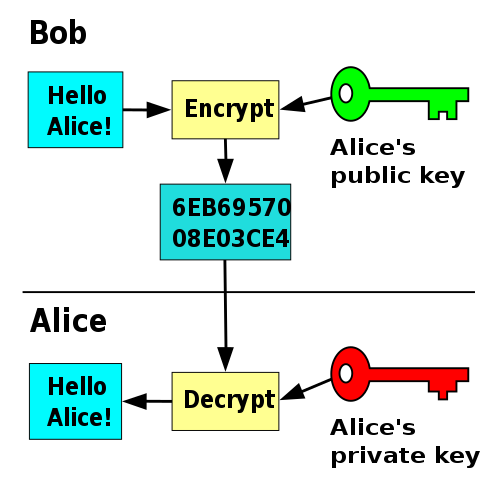

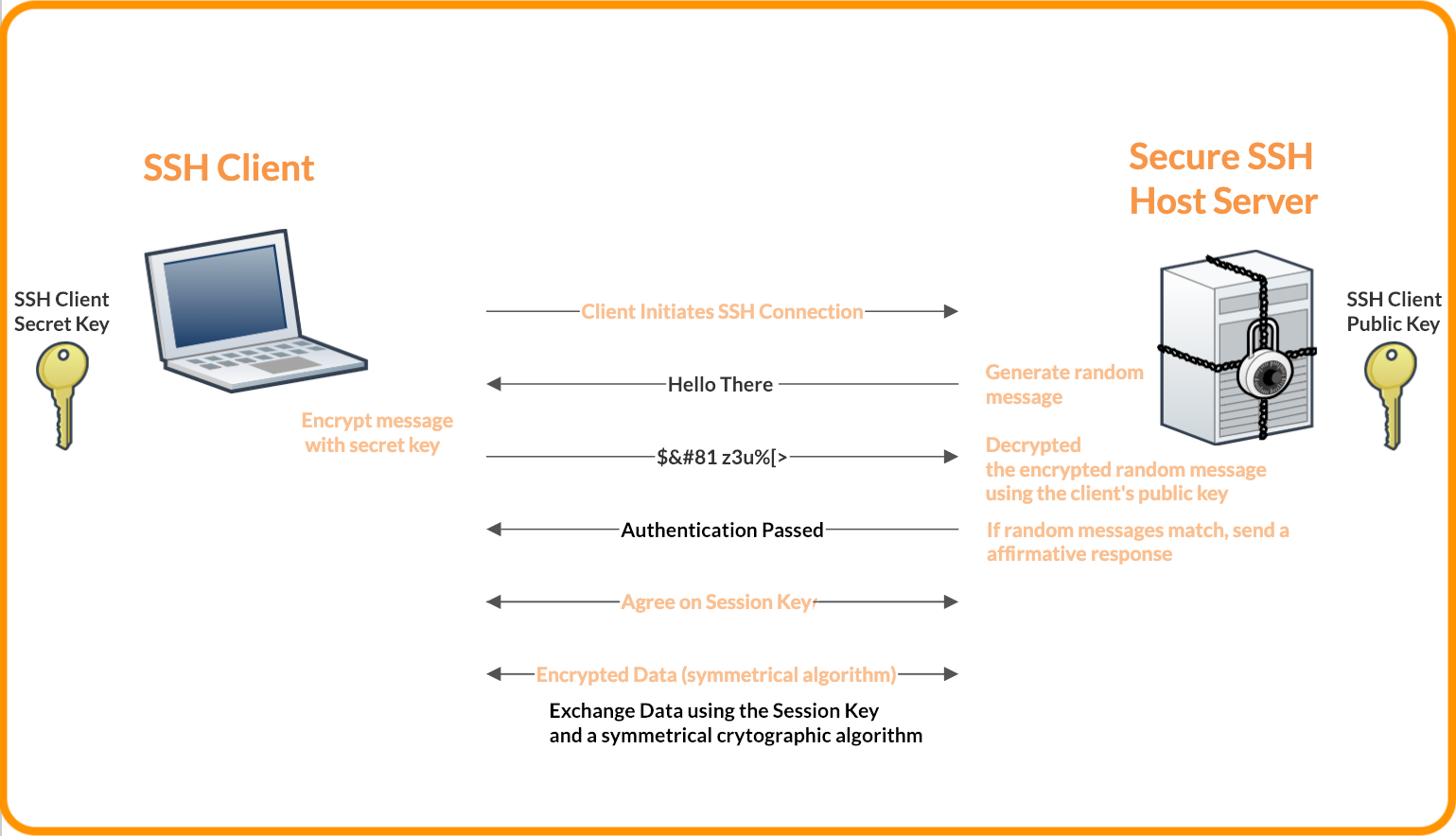
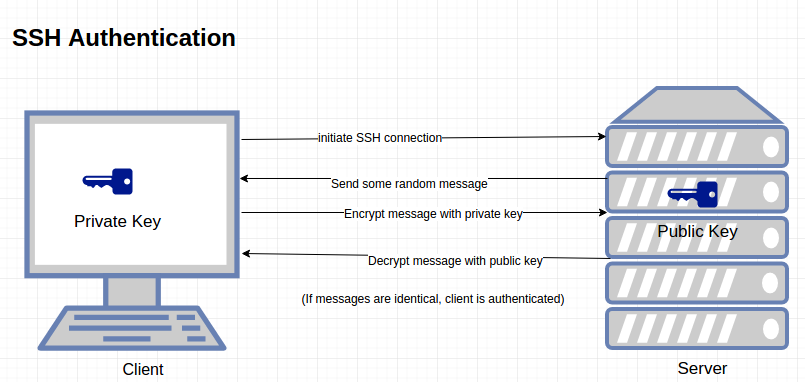
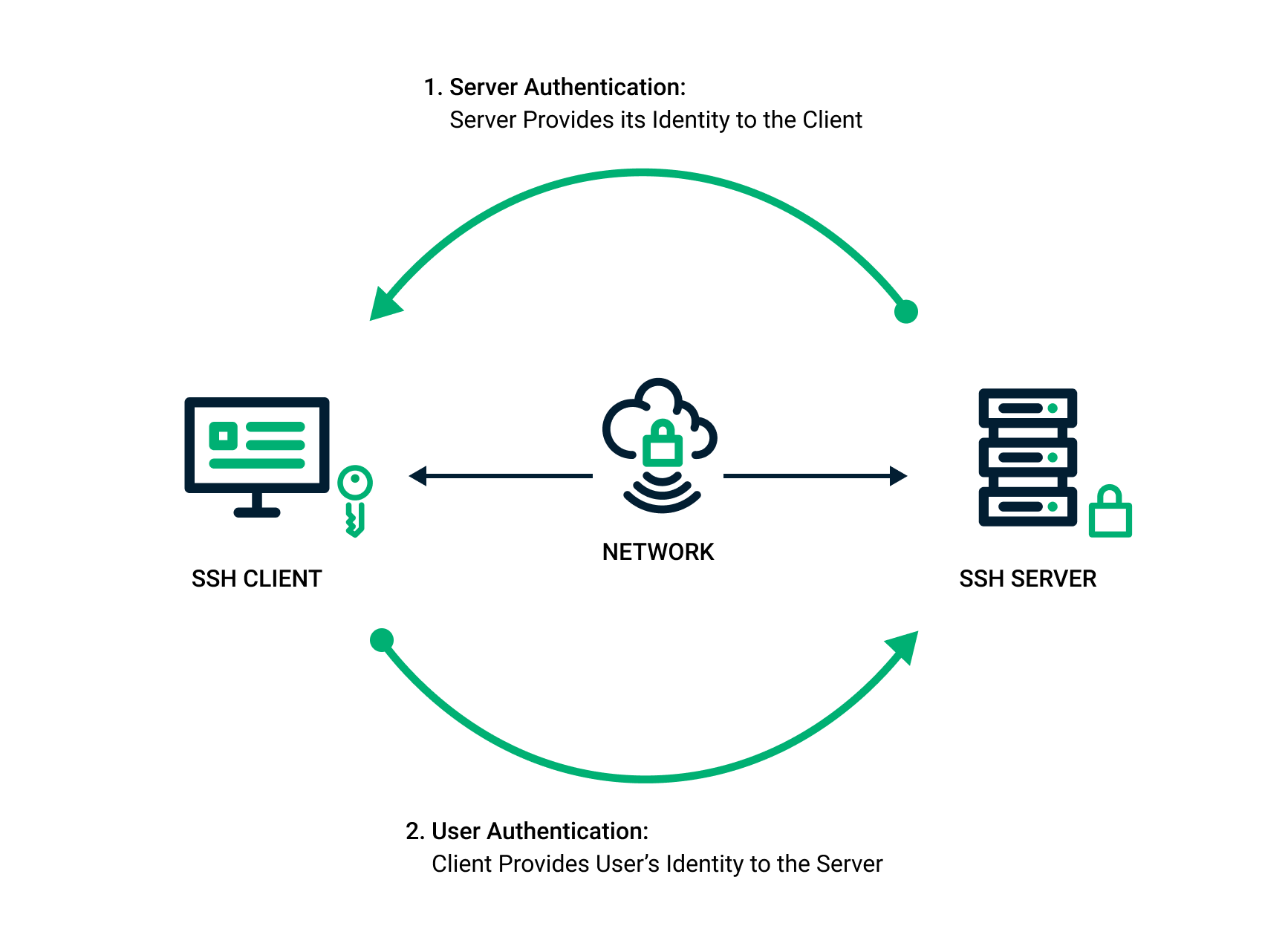

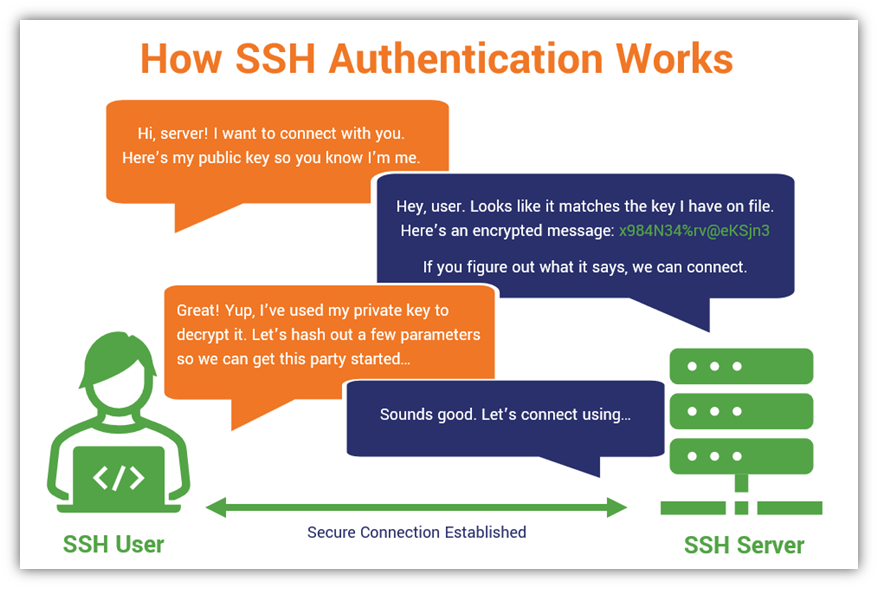

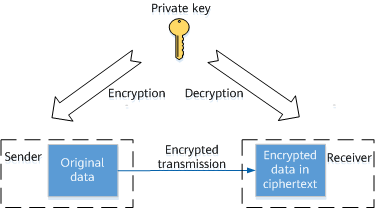
![ssh ] Public key vs. Private key | Chang Min Park ssh ] Public key vs. Private key | Chang Min Park](http://www.beyondthegeek.com/wp-content/uploads/2016/08/keys.gif)