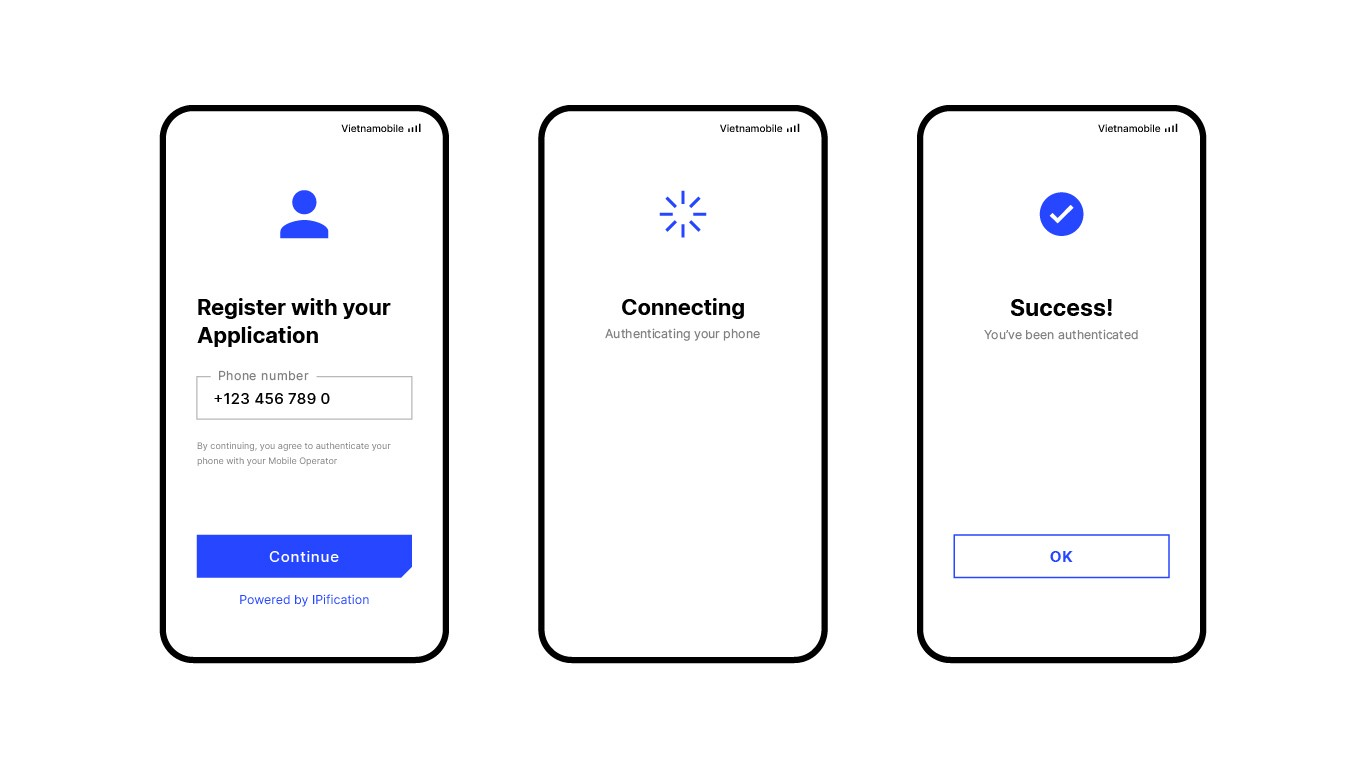
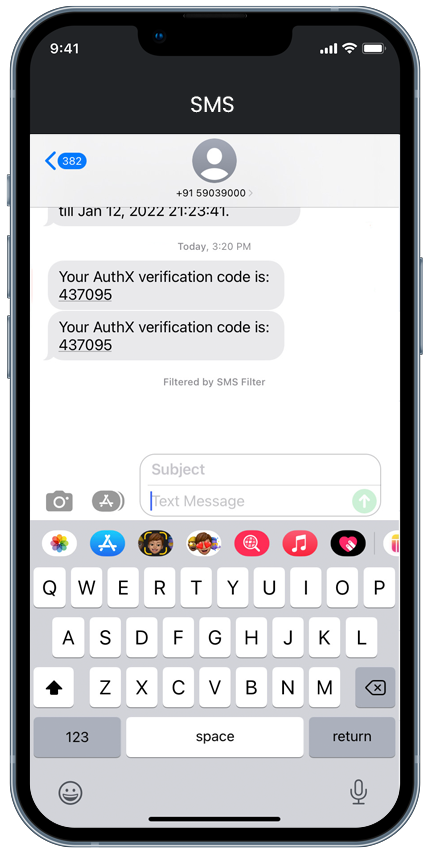
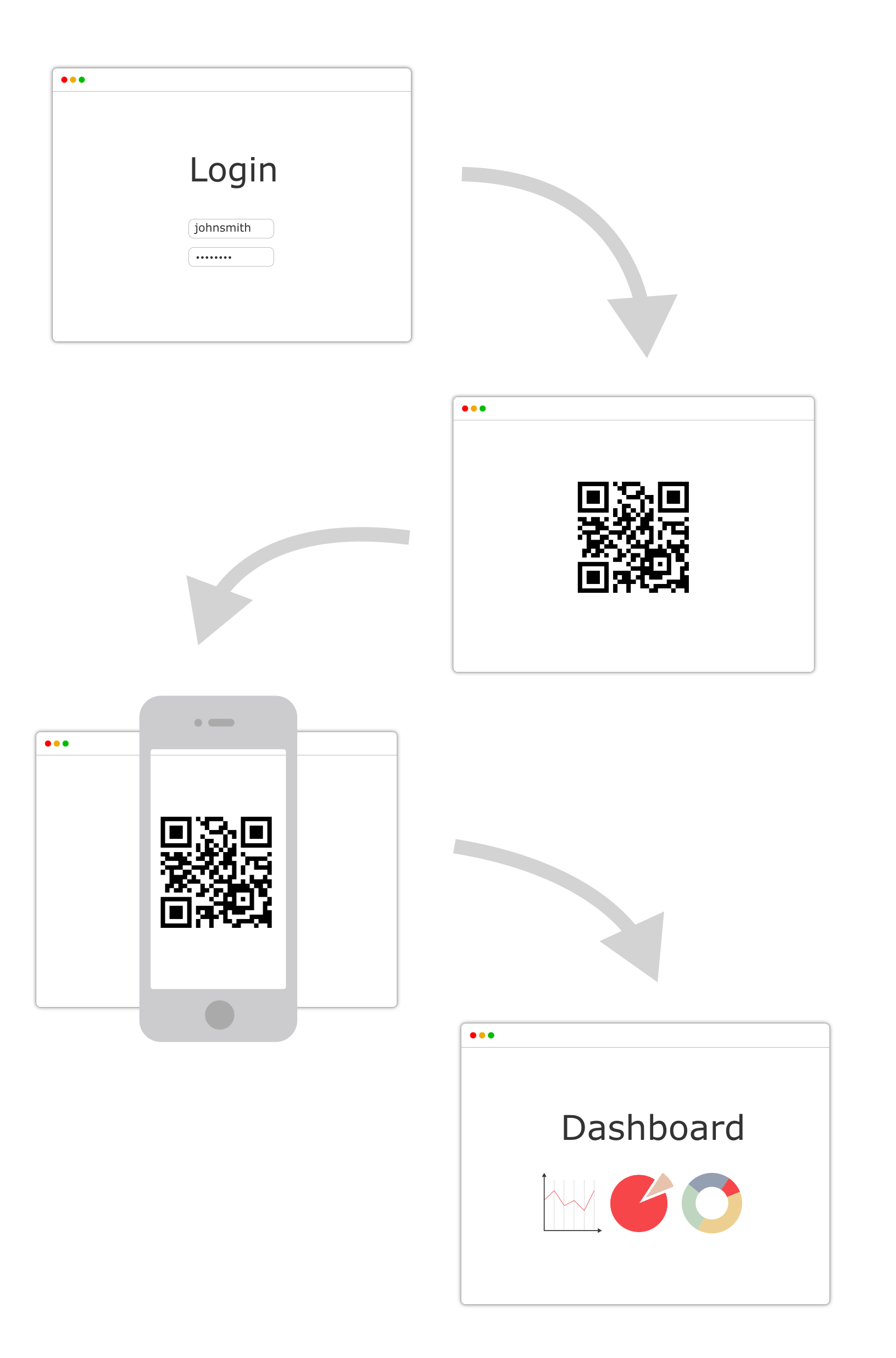
Two step authentication, 2-step Verification SMS code password concept. Smartphone with special 2FA software and tablet pc with multi-factor authentication safety and secure login form - MIDRANGE
Login Form on Smartphone, Mobile Authentication Stock Vector - Illustration of software, account: 134996313

What's the Best Form of Authentication on Your Mobile Device? - Directive Blogs | Directive Technology, Inc. | Otsego County, NY

Passwordless verification API transforms every mobile phone into a security token for zero trust access - Help Net Security