Encryption Cryptography Stock Illustrations – 3,415 Encryption Cryptography Stock Illustrations, Vectors & Clipart - Dreamstime

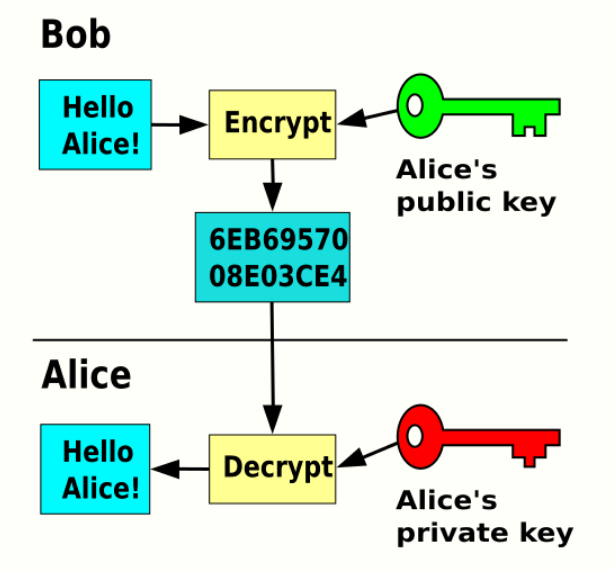
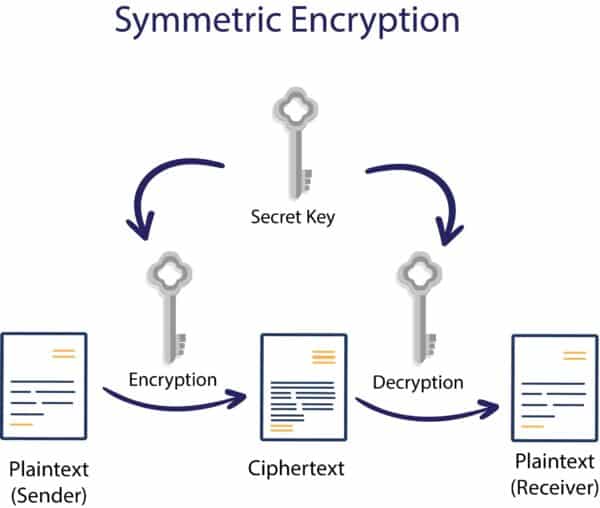
What is Cryptography in security? What are the different types of Cryptography? | Encryption Consulting

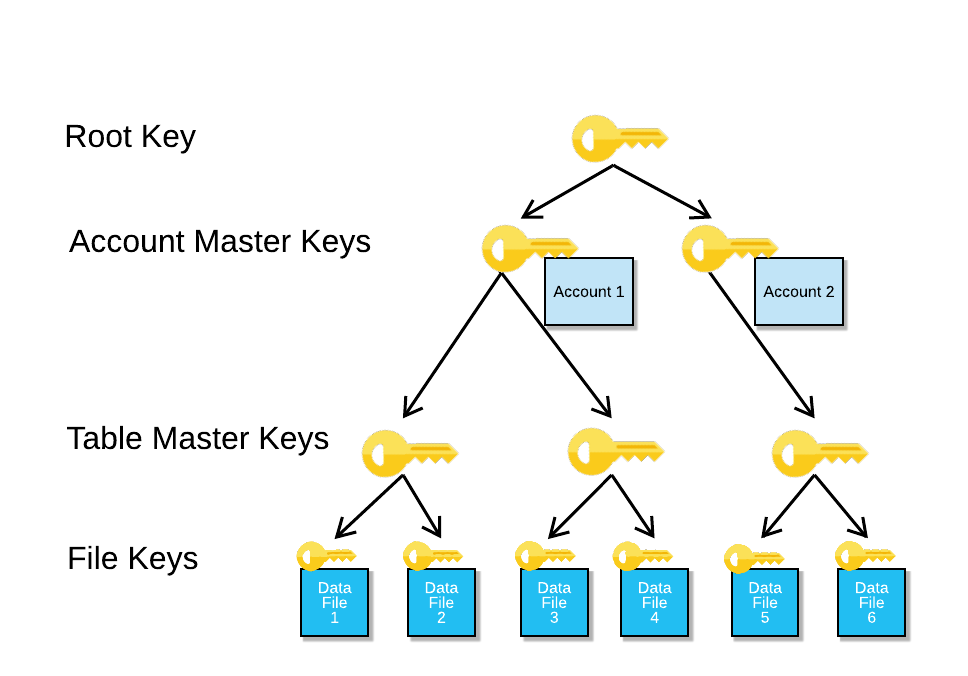
Blakley Secret Sharing. If you want to find out about other… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

Cryptography | Free Full-Text | Formalizing and Safeguarding Blockchain-Based BlockVoke Protocol as an ACME Extension for Fast Certificate Revocation
![PDF] Group key establishment protocols: Pairing cryptography and verifiable secret sharing scheme | Semantic Scholar PDF] Group key establishment protocols: Pairing cryptography and verifiable secret sharing scheme | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/04a94b19624f74759faea538486ef3fcec16837c/35-Figure3.3-1.png)
PDF] Group key establishment protocols: Pairing cryptography and verifiable secret sharing scheme | Semantic Scholar





![PDF] Safeguarding MTC at the Physical Layer: Potentials and Challenges | Semantic Scholar PDF] Safeguarding MTC at the Physical Layer: Potentials and Challenges | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/aac62c4dbc0e0e0ad339e3c99b0f63f65f52b4d1/6-Figure3-1.png)