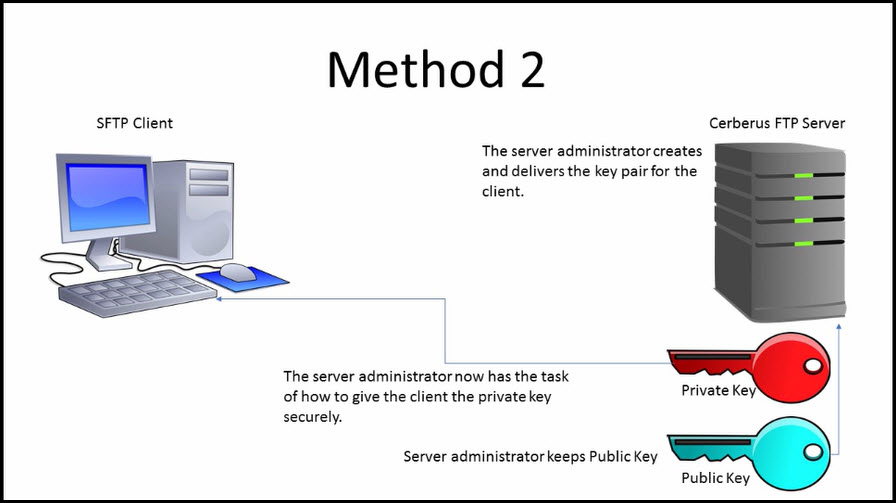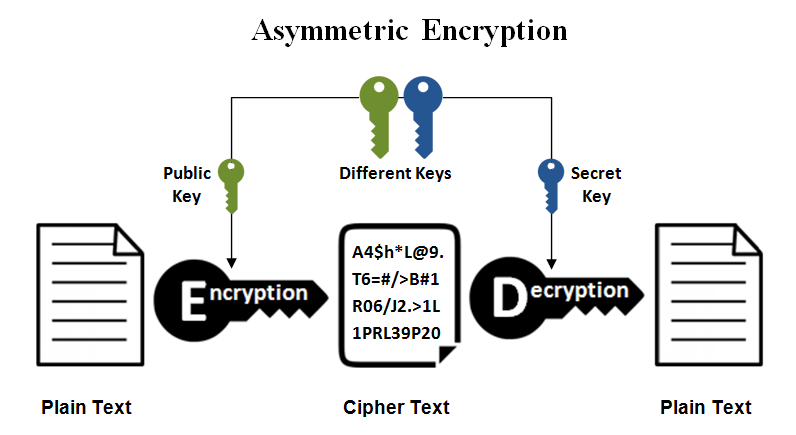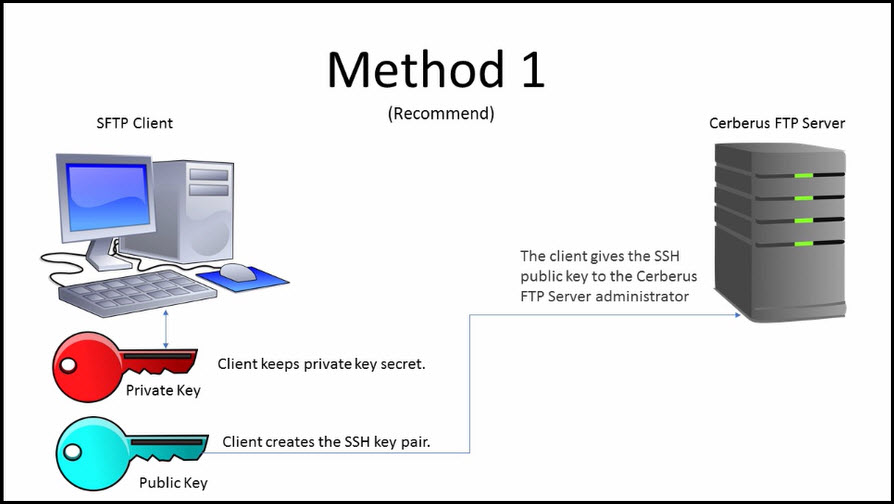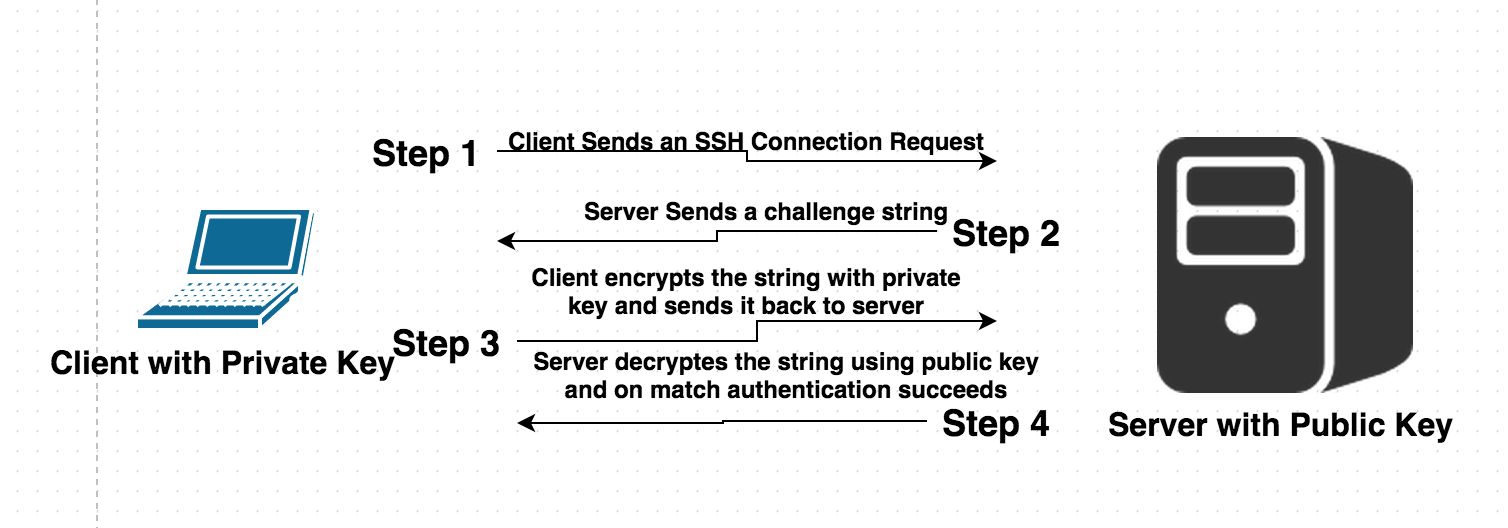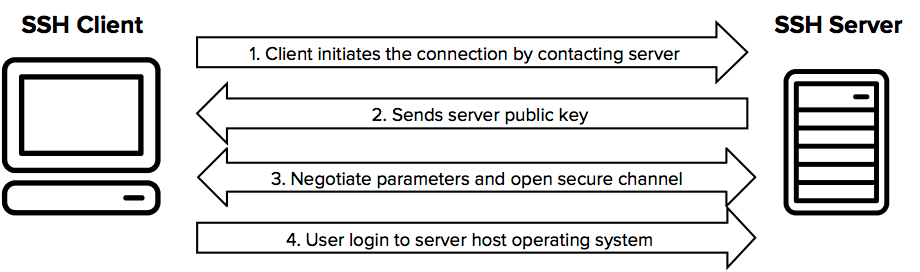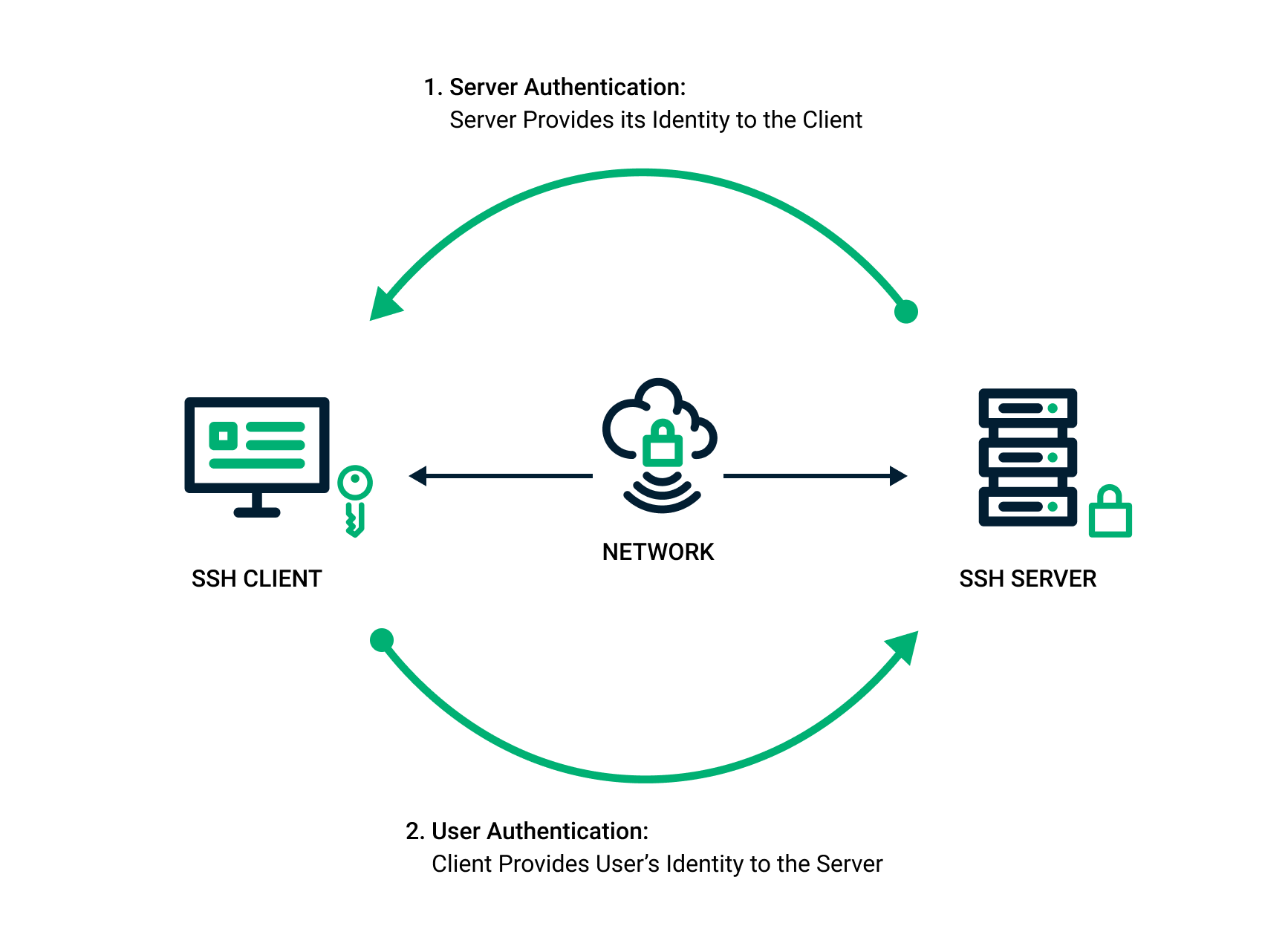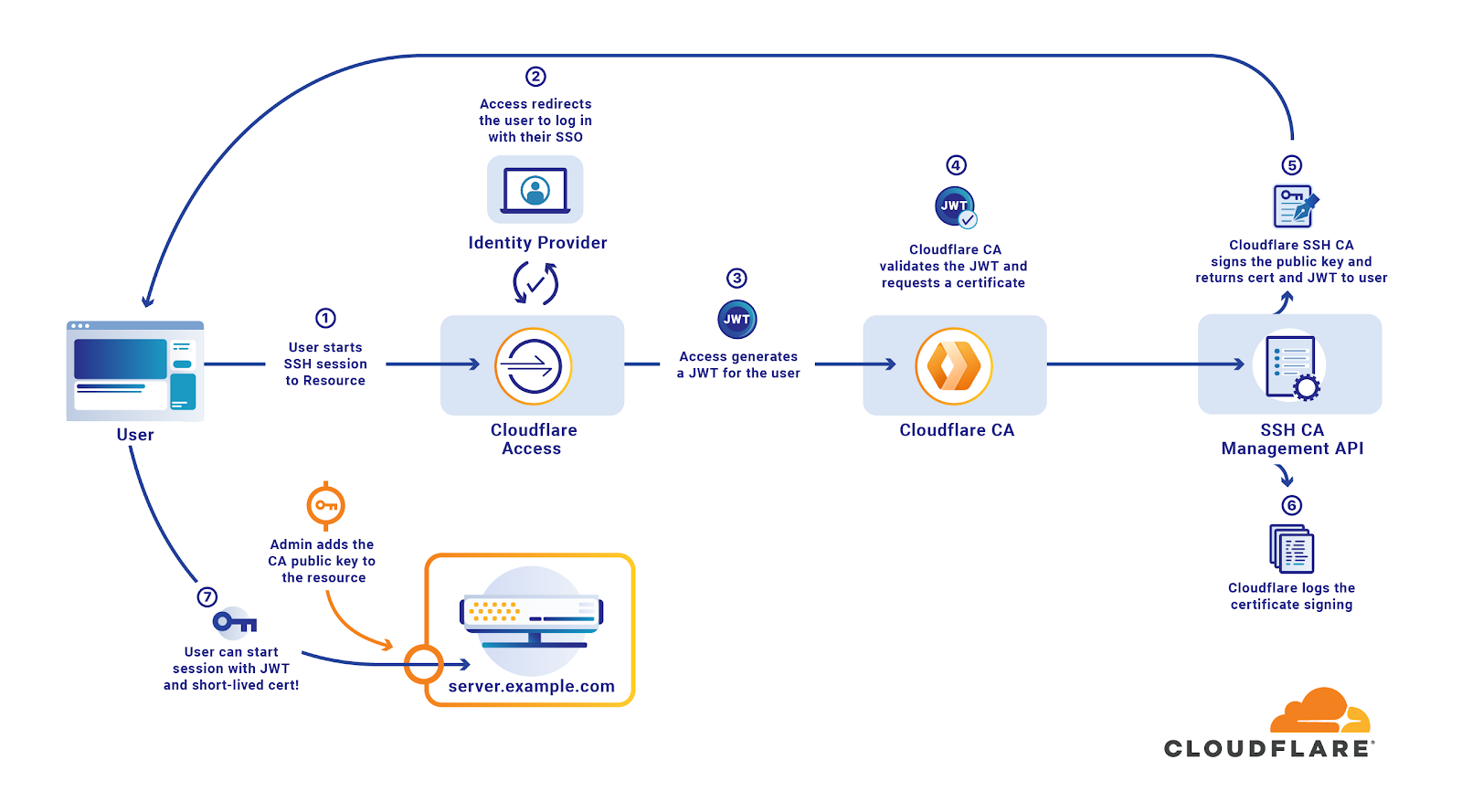
3.1.6 SSH connection setting method for Windows (when the PFM - RM host is running Windows and the monitored host is running UNIX) : JP1/Performance Management - Remote Monitor for Platform Description,

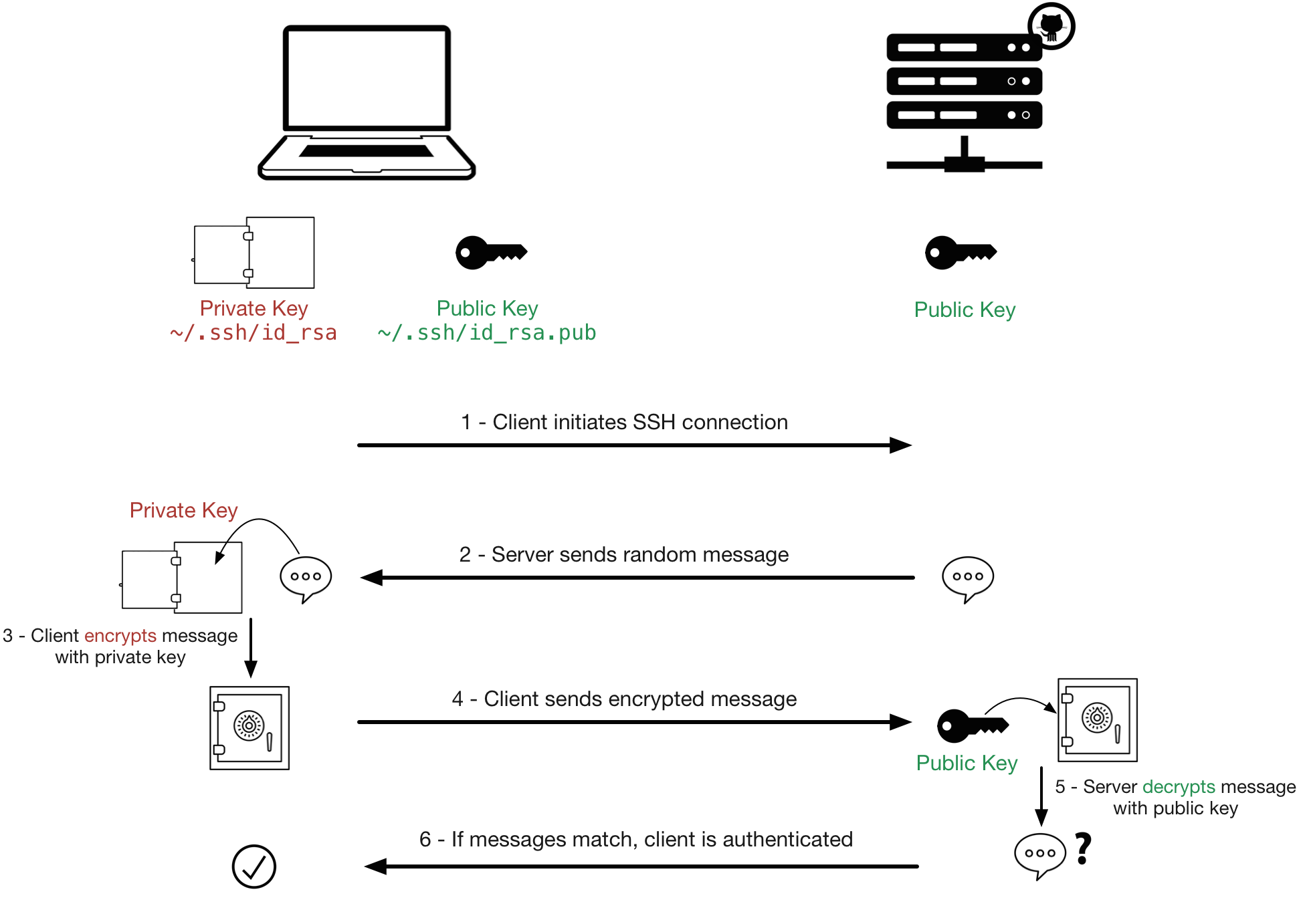
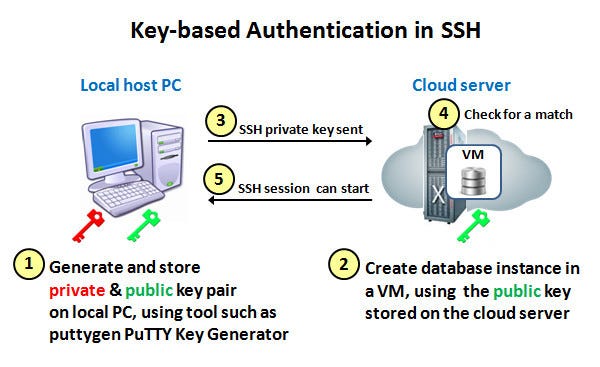
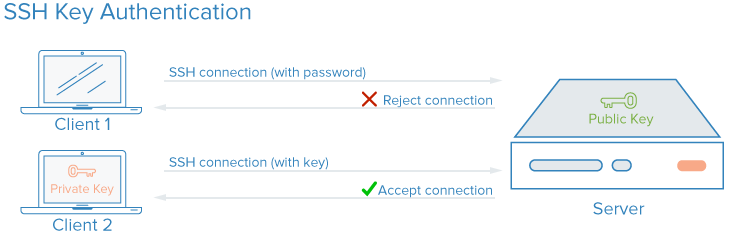
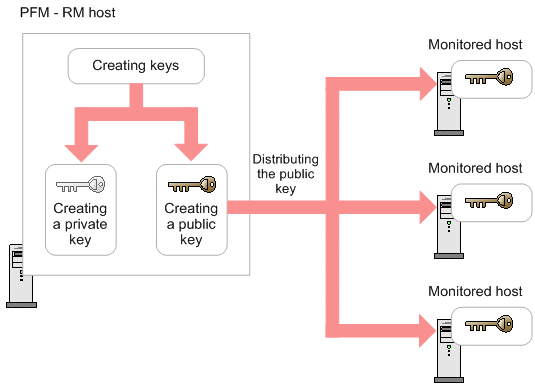
How to setup SSH key based authentication on Linux server - Reference Server - DYclassroom | Have fun learning :-)