Managed Custody Wallet Architecture & Private Keys Management - Frontal - Blockchain & Web3 Frontliners | Dubai, Abu Dhabi UAE | Middle East

Co-Inventor of Public Key Cryptography, Turing Award Winner, Alum | NYU Tandon School of Engineering

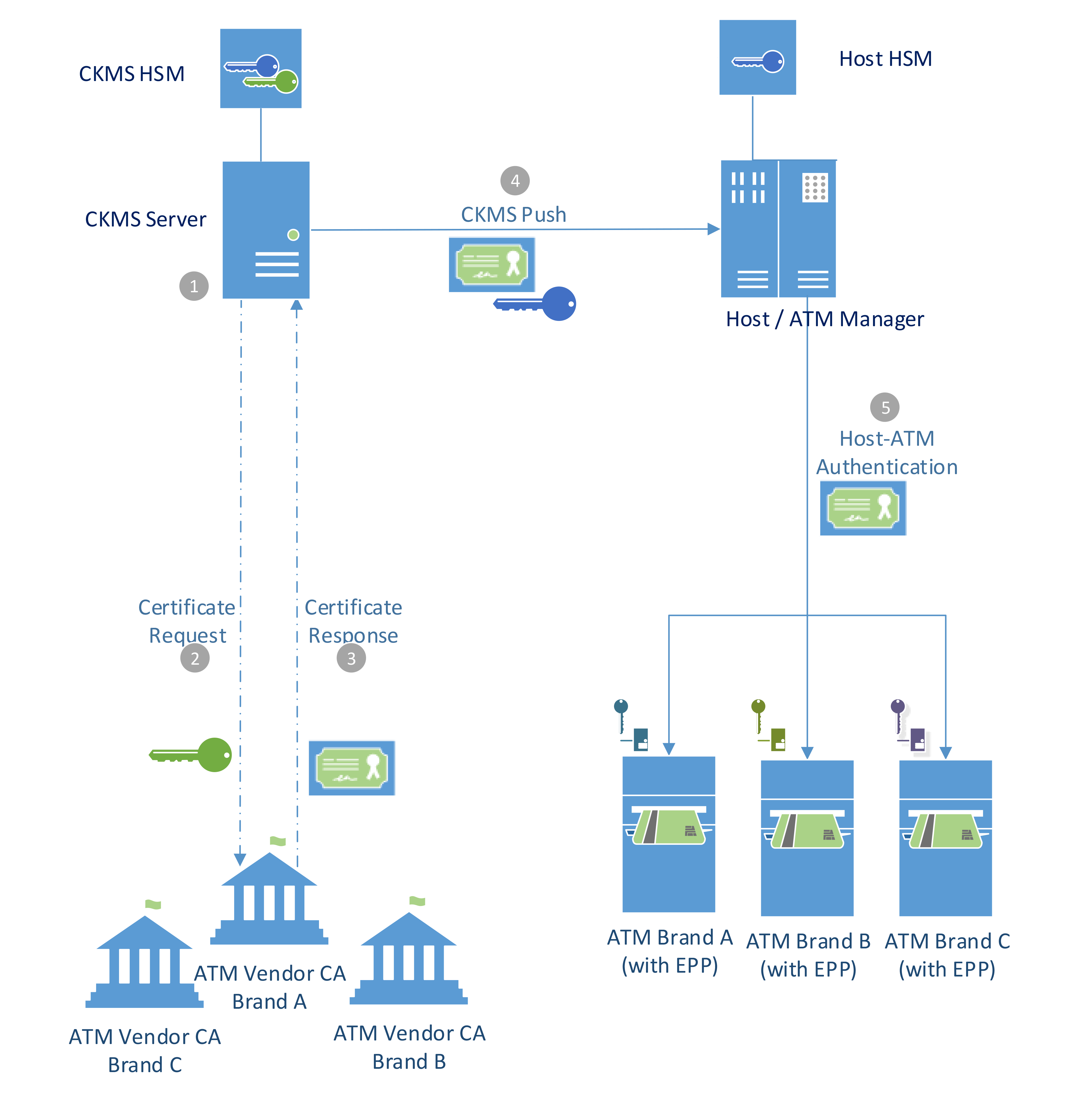

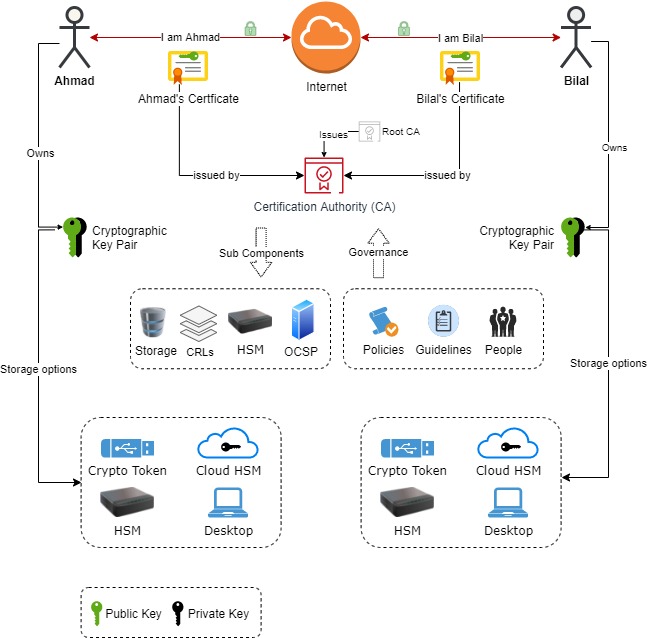

![PDF] Application of Biometric Key in Practical Secret Sharing for DNSsec | Semantic Scholar PDF] Application of Biometric Key in Practical Secret Sharing for DNSsec | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9d617a3c9d82c2432d96075f798331f95055acdf/2-Figure1-1.png)