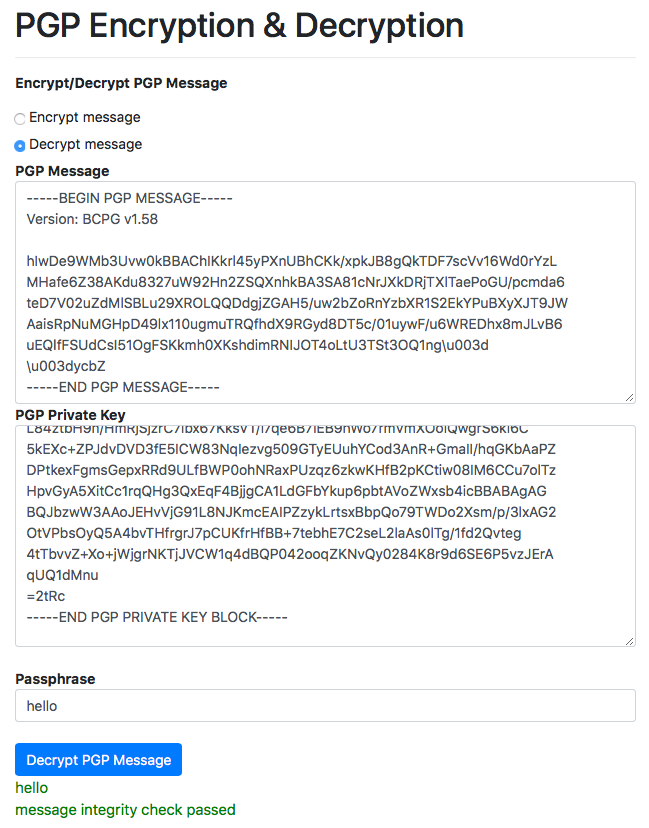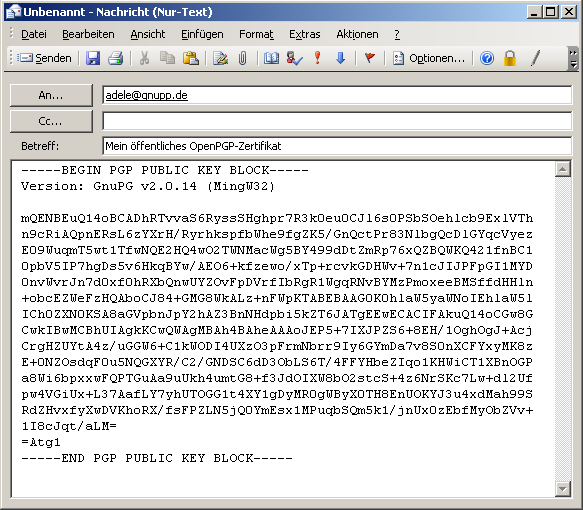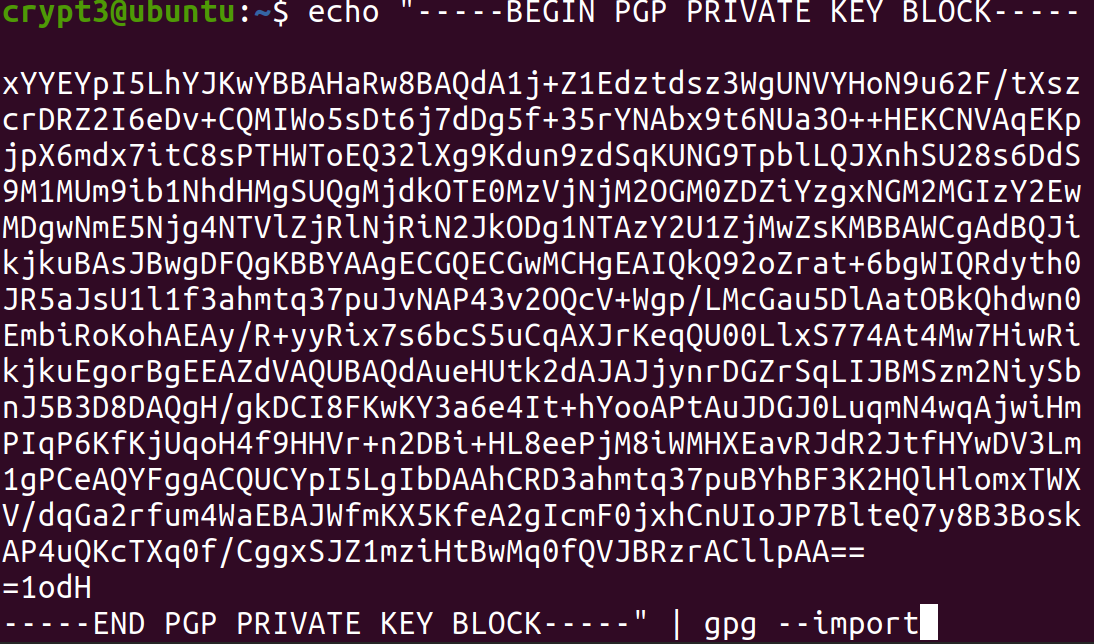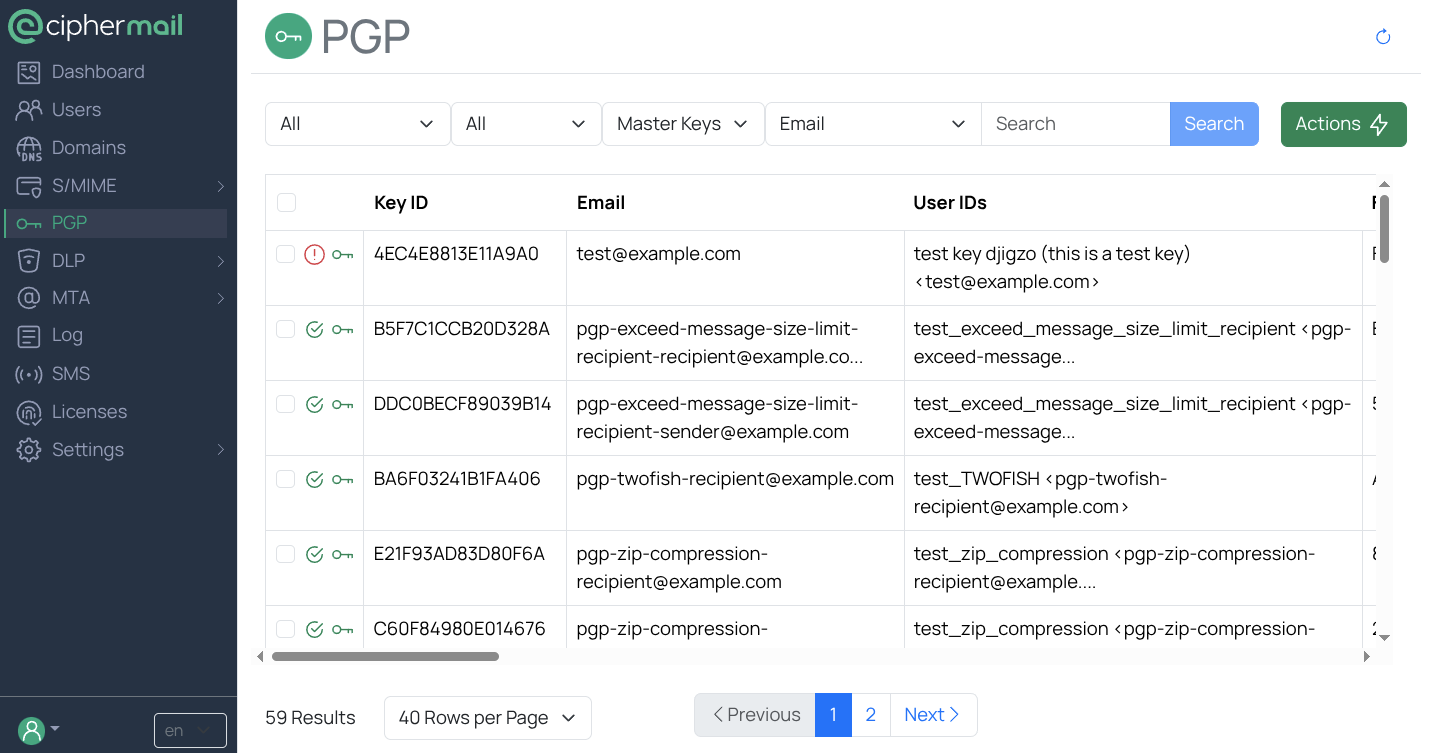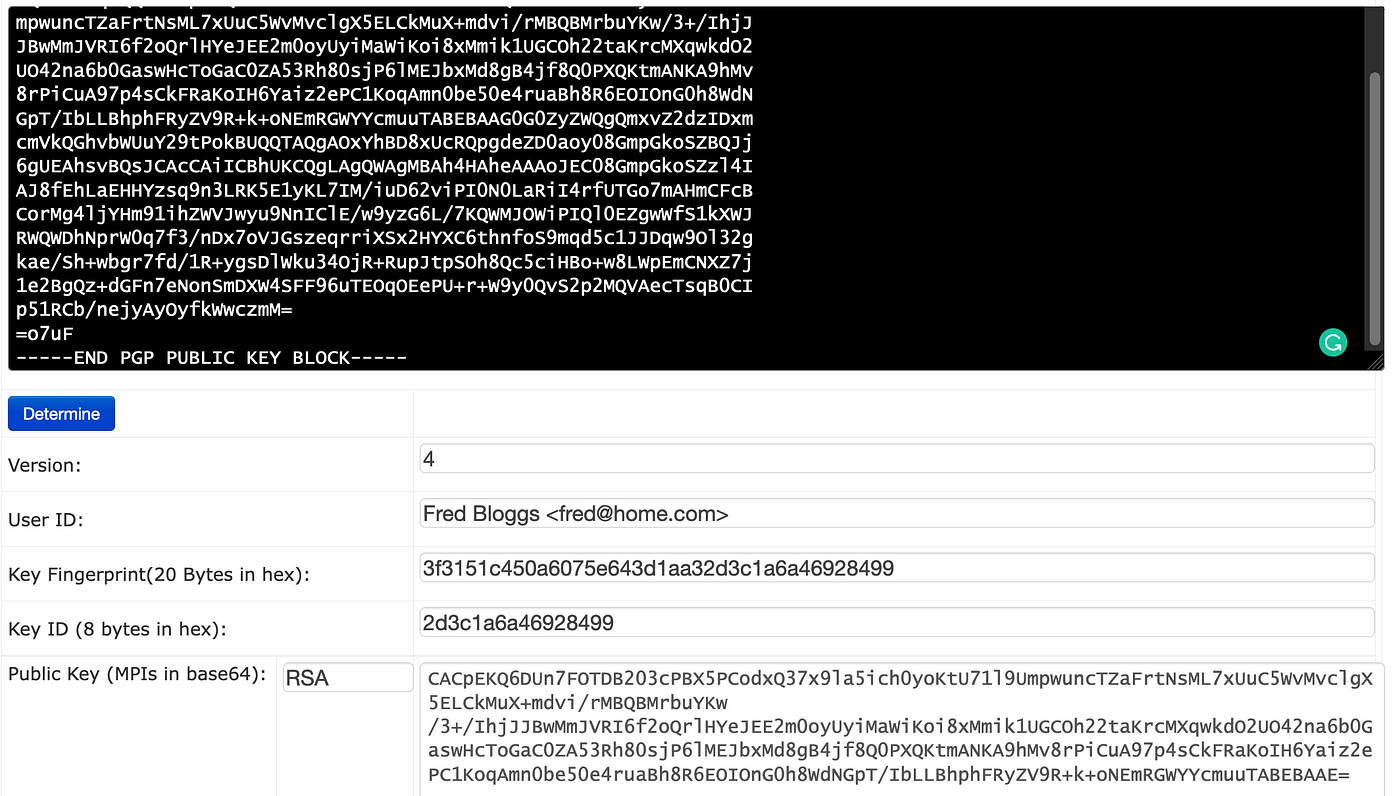
Privacy, Integrity and Trust: Some Day We Will Integrate These Into All Our Communications — The Mighty GPG | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Feb, 2023 | Medium

Step by step procedure Generate PGP keys and End to end iflow to encrypt-and-decrypt with Signatures | SAP Blogs
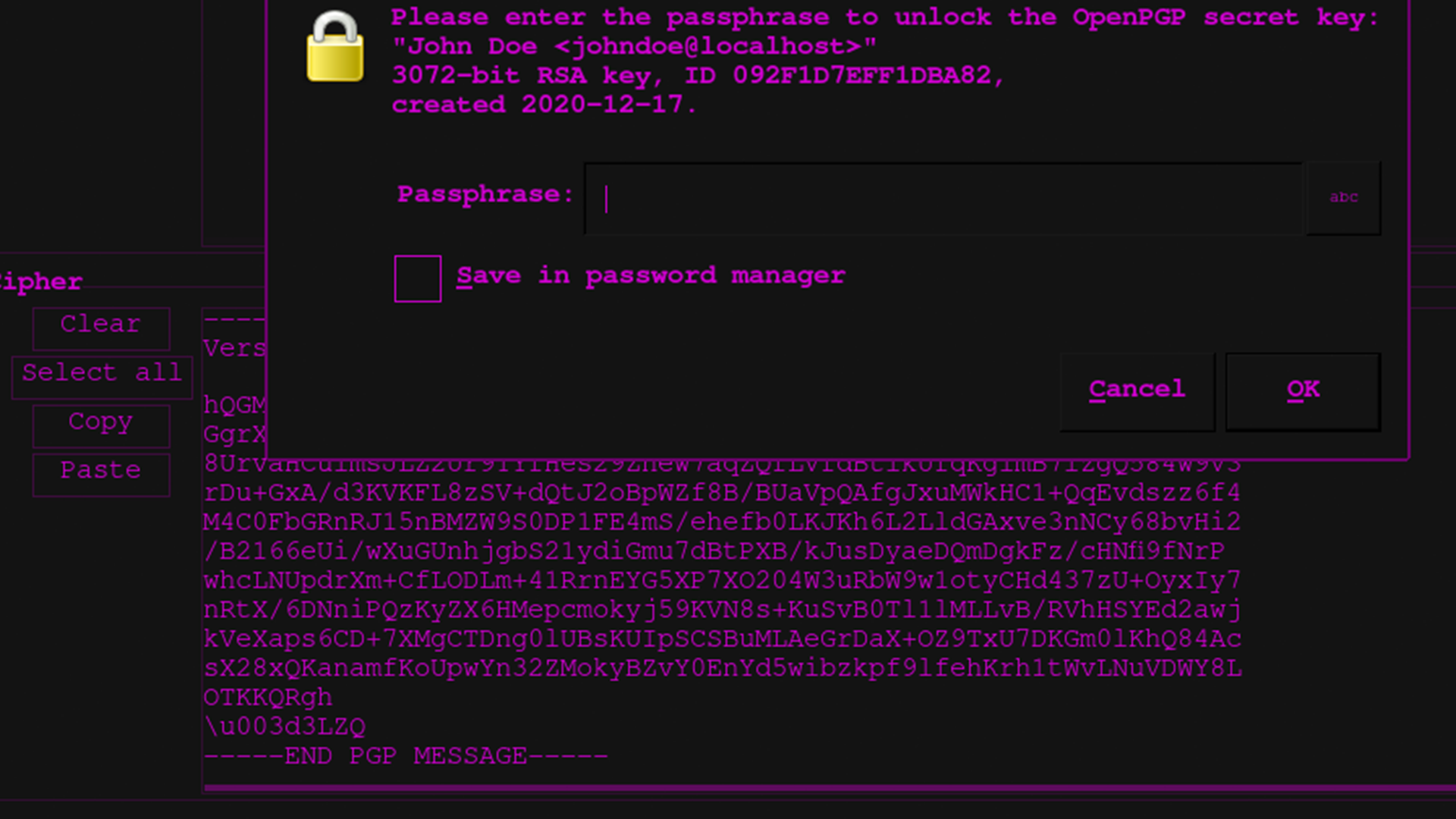
How To Make a PGP Keypair using GPG and Communicate In Absolute Privacy (Linux/Mac) Public & Private Keys + Encrypt & Decrypt Messages - Sick Codes - Security Research, Hardware & Software
![cryptography - How to get v12.0 to print PGP public key and secret key BLOCKS after generating a key pair using GenerateAsymmetricKeyPair[]? - Mathematica Stack Exchange cryptography - How to get v12.0 to print PGP public key and secret key BLOCKS after generating a key pair using GenerateAsymmetricKeyPair[]? - Mathematica Stack Exchange](https://i.stack.imgur.com/AZsn3.png)
cryptography - How to get v12.0 to print PGP public key and secret key BLOCKS after generating a key pair using GenerateAsymmetricKeyPair[]? - Mathematica Stack Exchange
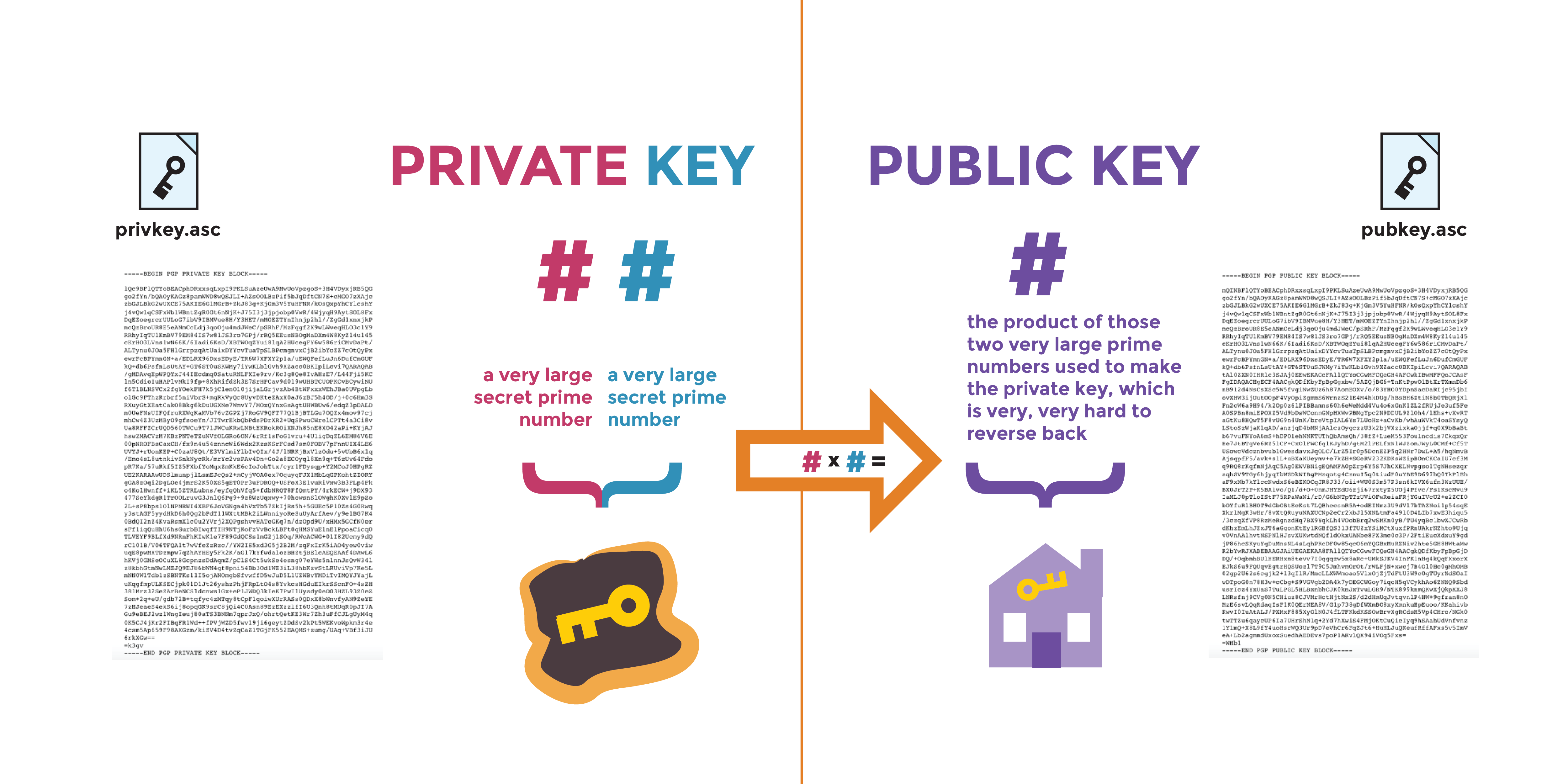
A Deep Dive on End-to-End Encryption: How Do Public Key Encryption Systems Work? | Surveillance Self-Defense
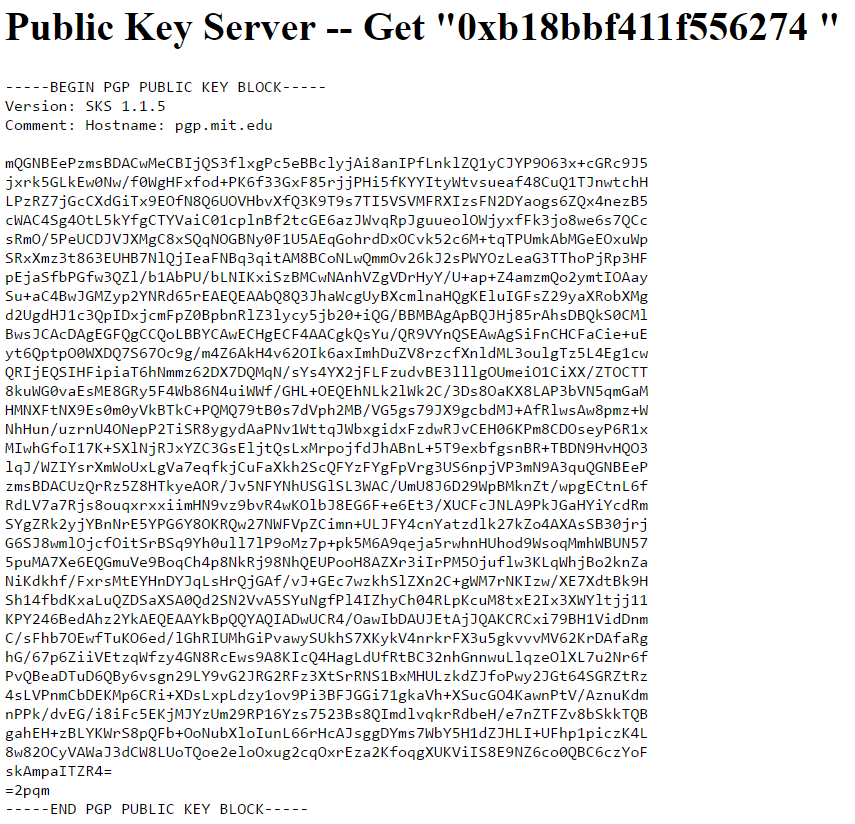
The hard evidence about Craig Wright's backdated PGP key — Step by step guide (for Windows users) | by hoaxchain | Medium