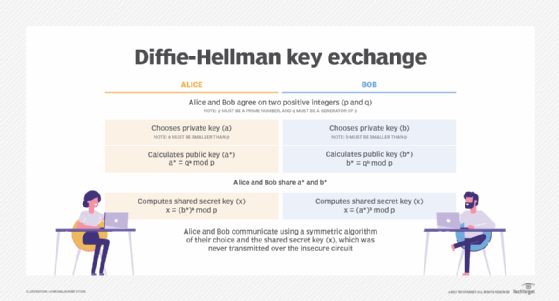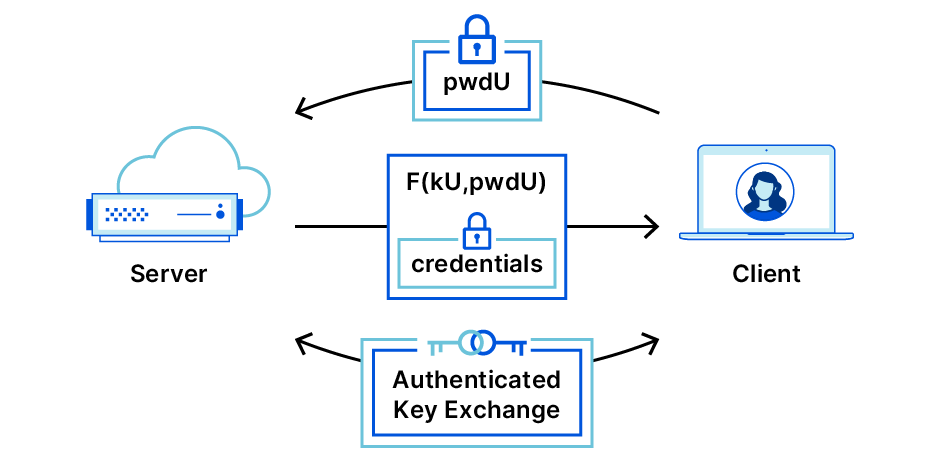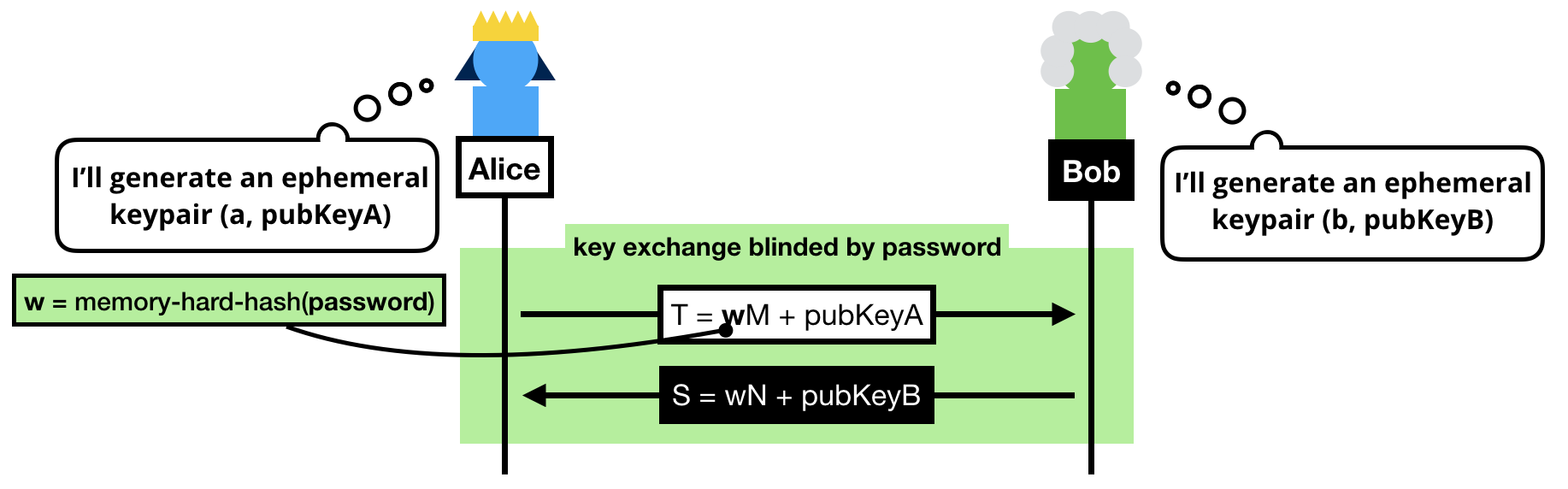
Cryptographic Techniques that Combine Data Protection and Ease of Utilization in the Cloud Computing Era | NTT Technical Review

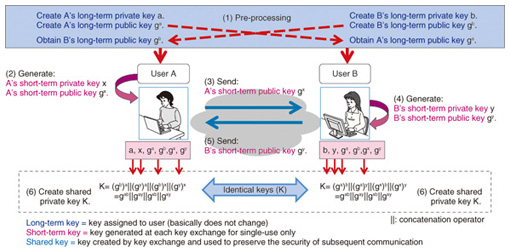
Authenticated Key Exchange I. Definitions I. MAP I. matching conversations II. oracles II. (I)KA II. AKEP2 III. AKEP2 Security I. Session Keys II. Perfect. - ppt download
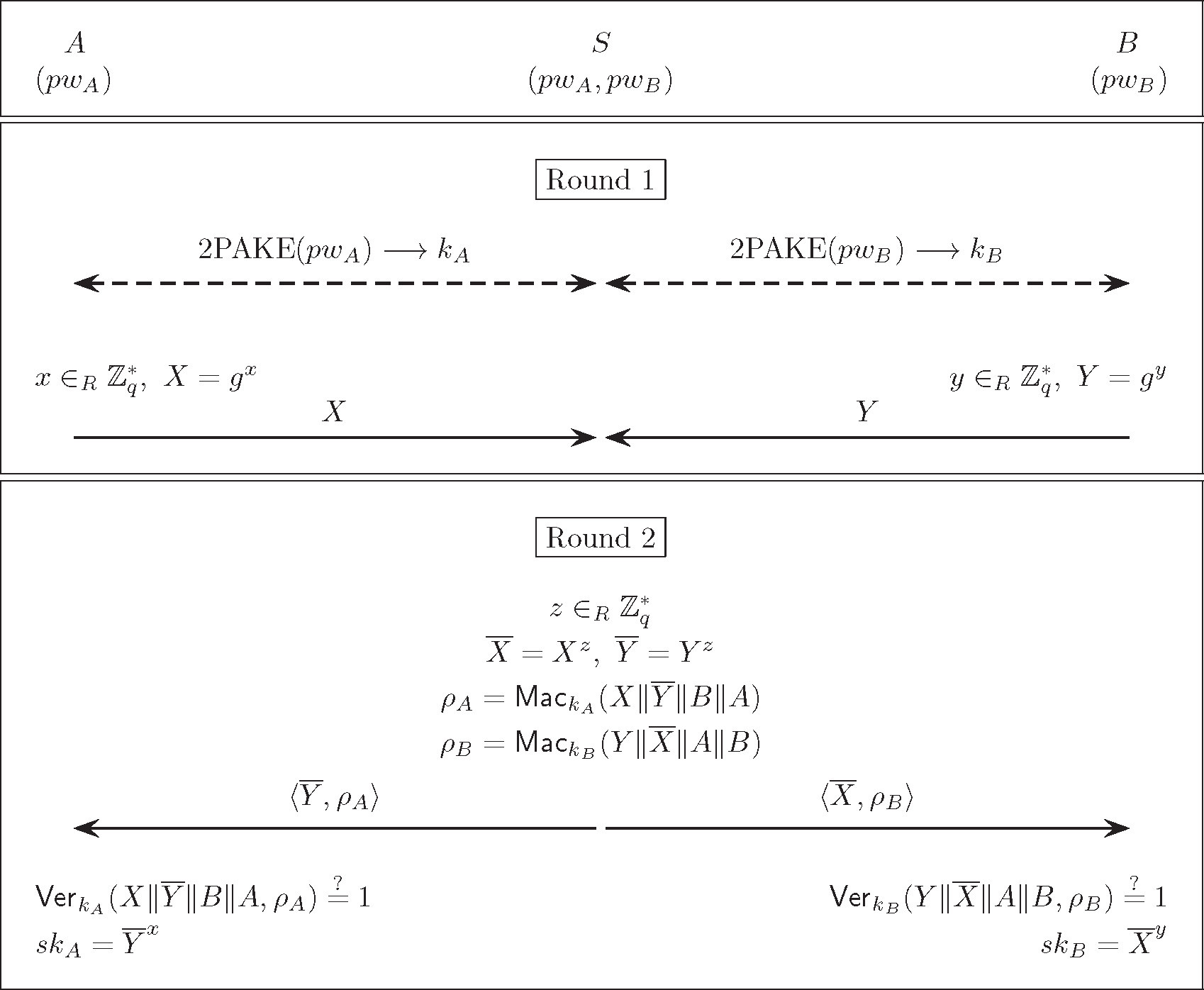
Symmetry | Free Full-Text | Two-Round Password-Only Authenticated Key Exchange in the Three-Party Setting
Cryptographic Authentication and Key Exchange - Security Assurance Scheme Research Team | Cyber Physical Security Research Center - AIST

Efficient Password-Authenticated Key Exchange from RLWE Based on Asymmetric Key Consensus | SpringerLink

Authenticated key exchange phase, divided into three parts, where we... | Download Scientific Diagram
GitHub - zyliutw/Password-based-Authenticated-Key-Exchange-from-Lattices: Implement Password-based Authenticated Key Exchange from Lattices protocol
![PDF] A Comparison of the Password-Authenticated Key Exchange Protocols, SRP-6a and PAKE2+ | Semantic Scholar PDF] A Comparison of the Password-Authenticated Key Exchange Protocols, SRP-6a and PAKE2+ | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/93af82343d6121e166488033b18899f70ed26b68/16-Figure2.1-1.png)
PDF] A Comparison of the Password-Authenticated Key Exchange Protocols, SRP-6a and PAKE2+ | Semantic Scholar