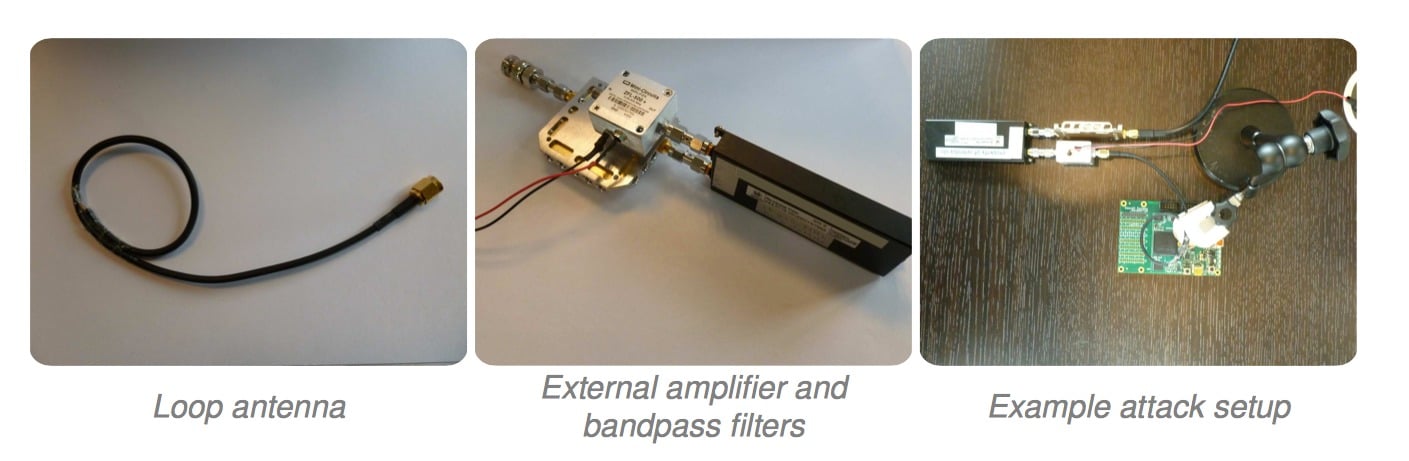
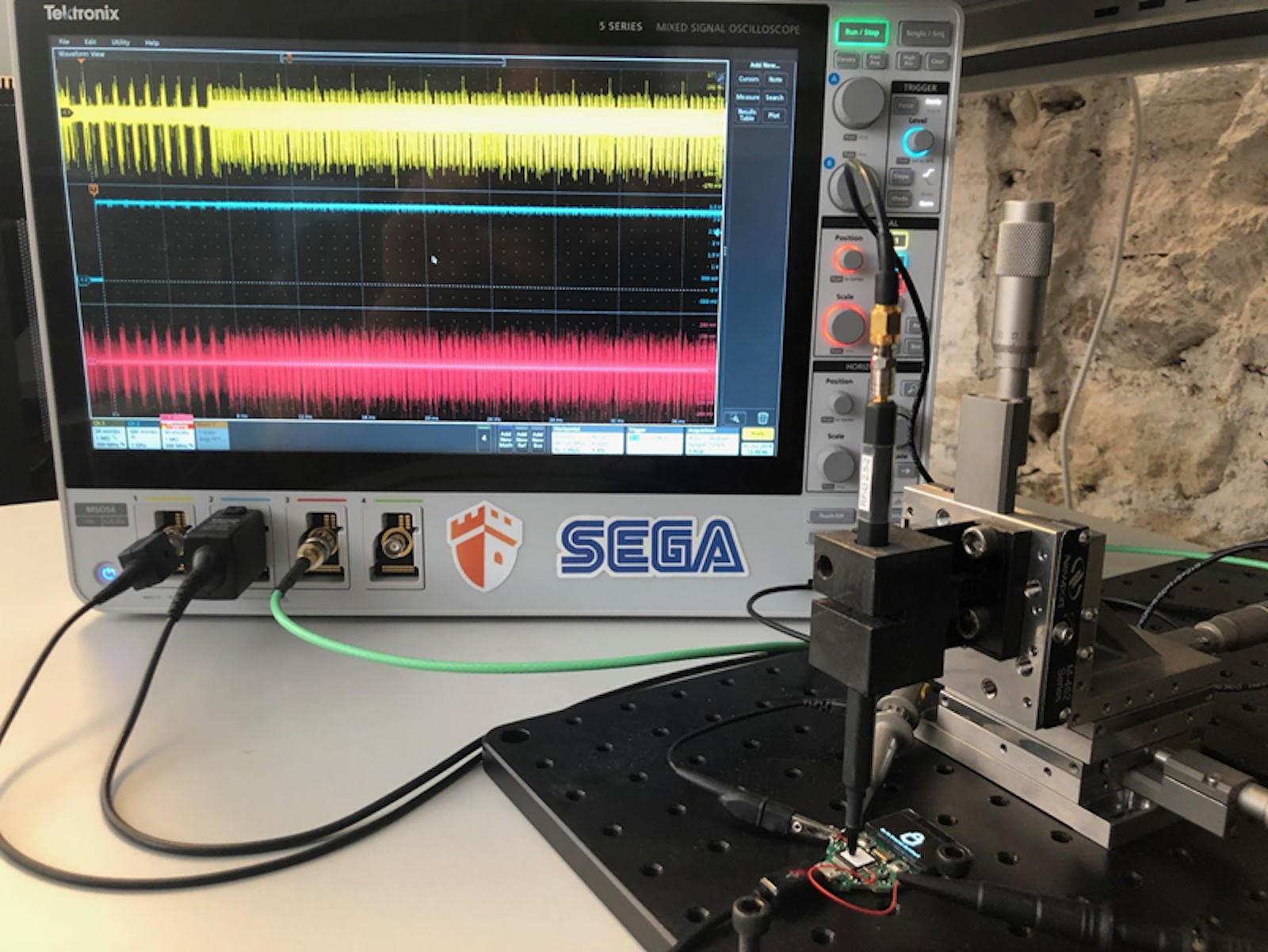
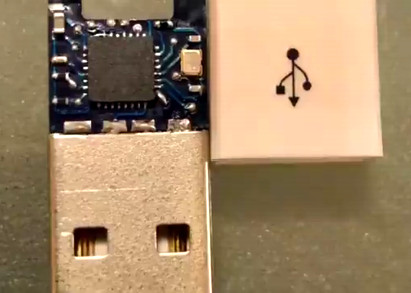
The ChipWhisperer capture hardware is used in this attack, although a... | Download Scientific Diagram

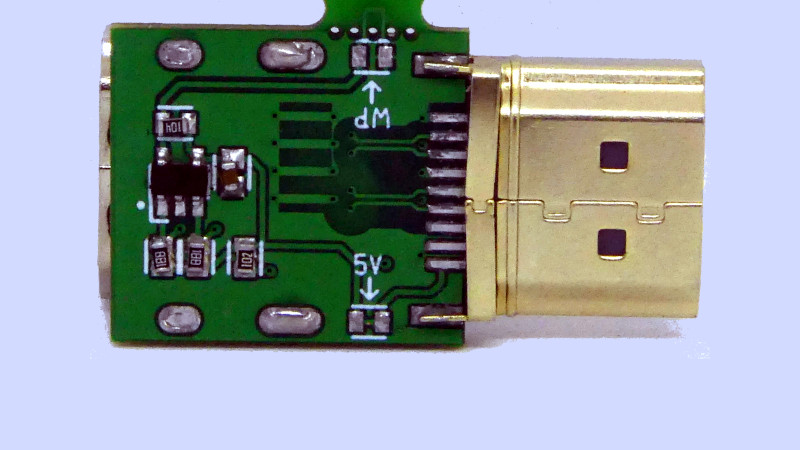
MG on Twitter: "After months of work, I am now holding the very first fully manufactured #OMGCable. I can't wait to get these up on https://t.co/mVYIMD3v7g Now time for a fully destructive
Bow to the USBsamurai: Malicious USB cable leaves air-gapped networks open to attack | The Daily Swig

Alarm and monitoring module GSM with GPRS functionality and control app + data cable: Amazon.de: Computer & Accessories